 Become a Partner
Already a partner ? Login
Become a Partner
Already a partner ? Login
Program
Partner Program Overview
Designed to deliver unparalleled customer value and accelerated mutual growth by harnessing partner expertise and ColorTokens cybersecurity technology.
Learn MoreInfrastructure
Quick Links
Case Study
Industry Solutions
Quick Links
Program
Designed to deliver unparalleled customer value and accelerated mutual growth by harnessing partner expertise and ColorTokens cybersecurity technology.
Learn MoreFeatured Topic
Newsletter
In May 2019, 4,000 flyers were stranded overnight at an Indian airport after technical glitches hit check-in, reservation, and baggage handling systems. In September 2018, passengers had to read flight times off whiteboards for two days as the flight information screens at Bristol Airport in the U.K. went blank.
The reason? Both these airports were under cyberattacks.
Unfortunately, such attacks on airports aren’t isolated incidents. A report from ImmuniWeb found that “97 out of the world’s largest 100 airports have security risks related to vulnerable web and mobile applications, misconfigured public cloud, Dark Web exposure or code repositories leaks.” As a result, aviation systems frequently find their data and operations at risk from complex cyberthreats.
Airports process data from millions of passengers and cargo shipments every year. They have access to customers’ personally identifiable information (PII) and payment details, as well as employee data and biometrics. Moreover, since airports are part of a country’s critical infrastructure, breaches can have significant and widespread consequences beyond financial loss and reputational damage. In March 2020, hackers attacked two San Francisco Airport websites and stole usernames and passwords of staff and contractors. To avoid any adverse events, the airport had to pull down the affected websites and issue a forced password reset before bringing them back online.
For passengers’ comfort and for operational efficiency, airports rely heavily on technology and automation for ticketing, check-ins, Wi-Fi, personnel authentication, access controls, surveillance, and staff management. Since airport systems are interconnected, unsecured data flow in this network expands the attack surface.
The various manned and unmanned systems in an airport also increase the attack surface. Ticketing and POS terminals, baggage handling, e-boarding stations, parking systems, site management, and other types of workstations managing critical functions are vulnerable to internal as well as external cyberthreats. In addition, data sharing with third-party vendors adds another layer of security complexity.
Airports face are a range of cybersecurity threats. The most common cyberthreats that the aviation industry faces are:
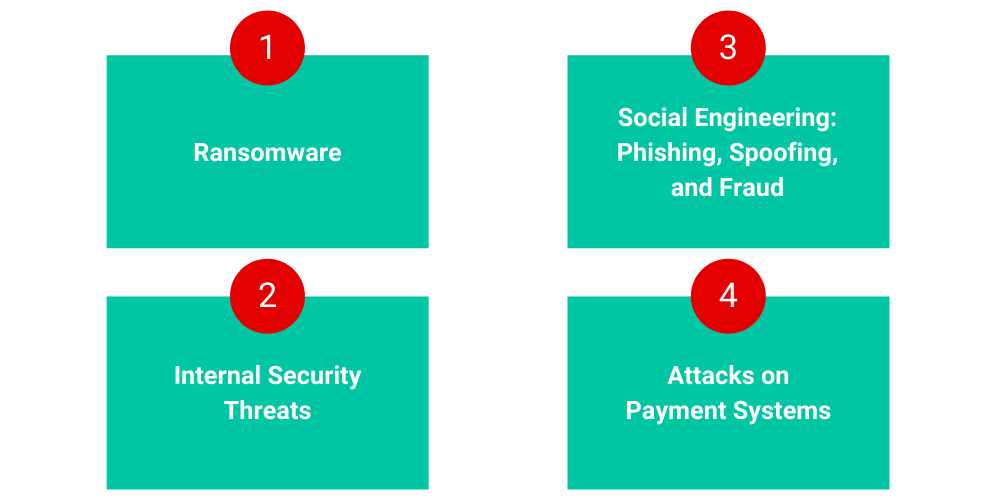
In a ransomware attack, a cybercriminal could encrypt and hold hostage digital assets, such as files or computer systems, and then demand ransom from the victim to regain access. For example, in January 2020, cybercriminals hacked into an Albany Airport’s third-party contractors’ networks and then spread the malware to the airport’s management servers. The airport had to pay off those hackers to restore operations.
An employee at Heathrow Airport posed a security threat by failing to store data in secured formats, and then losing a USB stick containing sensitive data, which was later found by a member of the public. Reports said that the memory stick contained information about the Queen’s routes and personal data of about 50 of the airport’s security staff.
Airport employees and customers could fall victim to phishing emails by clicking on infected links. In July 2020, the FBI warned of fraudulent domains that spoofed websites of American airports. Fraudsters can pose as airport authorities, or affiliated entities, to defraud unsuspecting customers and vendors. In 2018, hackers breached an Australian company that issued security identity cards to airport staff for accessing planes and other restricted airport zones, seriously compromising airport security.
Hackers stole payment card details and other personal information of half a million British Airways customers. Such leaks can result in regulatory actions, reputational damage, and the potential loss of customers. For the above incident, British Airways paid £183 million in GDPR fines for lax data security.
Here are five essential best practices that can help airports strengthen their security posture and defend their networks against cyberattacks and data breaches.
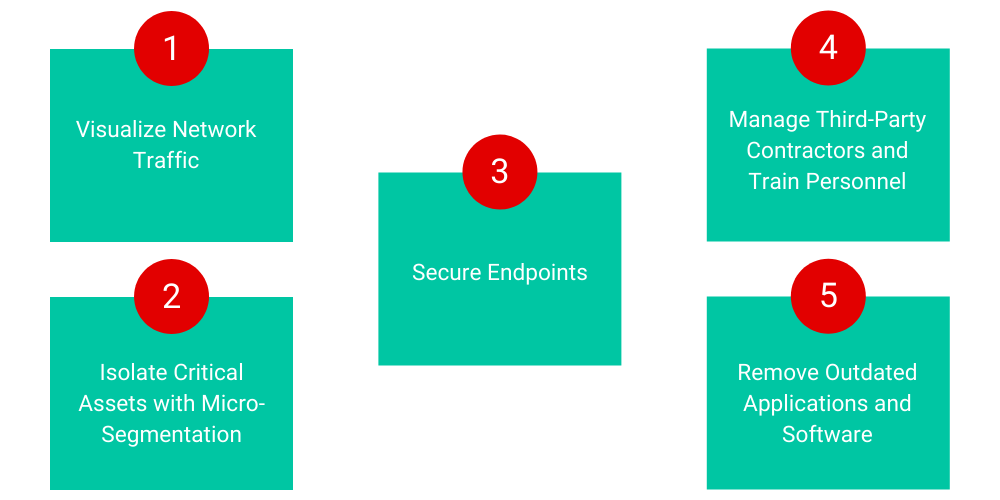
Airport security teams need in-depth visibility of network traffic across the airport’s on-premise users, endpoints, and applications, as well as cloud workloads. ColorTokens Xshield enables centralized, granular visibility into an airport’s critical applications and servers in real-time, helping to identify suspicious connections. Risk metrics and analytics empower network admins to continuously assess and improve the security posture.
Airports should implement a zero trust security policy and separate transactional, application, and passenger database environments through microsegmentation. With ColorTokens Xshield, an airport’s infosec team can apply microsegmentation policy templates across its data centers and multi-cloud environment. This protects the network against lateral threats and reduces the attack surface, without requiring time-consuming firewall configurations. Through a centralized platform for multi-vendor infrastructure, the airport can secure its crown jewels by enforcing zero trust-based access to internal and third-party contractors.
Airports should allow access to critical and sensitive information strictly on a need-to-know basis and restrict unnecessary data flow between endpoints. They have to monitor software, communication networks, and other sensitive IT areas for any anomalous behavior.
ColorTokens Xprotect helps airports make their terminals and endpoints tamper-resistant. Airports can increase security by proactively locking down check-in kiosks, ticketing systems, building, and video management systems, and airport operational control centers to prevent breaches caused by malware, ransomware, and zero-day attacks. Legacy desktops and unpatched servers can also be securely locked down, even when they are offline.
Airports and airlines have data-sharing obligations with various regulatory and government agencies. They also have business partners and third-party service providers who interface with customer data. One weak link is all it takes for the entire system to get compromised. The aviation industry must put in place a policy to ensure that the partners and contractors who get access to such data have a robust cybersecurity infrastructure.
Information security leaders should ensure that all airport personnel and external consultants undergo cybersecurity and anti-phishing training. The staff must know that they should report emails from unknown URLs and not click on any links or open any files in such emails. They shouldn’t store data in unencrypted, unsecured formats. USB sticks, external drives, workstations, POS systems, and all other devices should be kept safe and protected by strong passwords that are updated frequently.
It’s important that airports keep all software and applications current and swiftly apply available security patches. Hackers constantly look for loopholes to launch zero-day attacks. The airport cybersecurity team must be on its toes to immediately secure any vulnerabilities that it discovers.
Malicious threat actors frequently target airports to gain access to customer data or to extort ransoms. ColorTokens helps airports protect their critical assets and fend off sophisticated attacks with its zero trust architecture-based solutions. ColorTokens Xtended ZeroTrust™ Platform simplifies cybersecurity for aviation networks and protects workloads, endpoints, applications, and users from known and unknown cyberthreats.
By submitting this form, you agree to ColorTokens
Terms of Service and
Privacy Policy