 Become a Partner
Already a partner ? Login
Become a Partner
Already a partner ? Login
Program
Partner Program Overview
Designed to deliver unparalleled customer value and accelerated mutual growth by harnessing partner expertise and ColorTokens cybersecurity technology.
Learn MoreInfrastructure
Quick Links
Case Study
Industry Solutions
Quick Links
Program
Designed to deliver unparalleled customer value and accelerated mutual growth by harnessing partner expertise and ColorTokens cybersecurity technology.
Learn MoreFeatured Topic
Newsletter
The ColorTokens Xtended ZeroTrustTM Platform is a cloud-based, SaaS-delivered, software-defined platform for hybrid networks that natively integrates Zero Trust access, endpoint protection and identity-based segmentation in a single platform, to simplify the adoption of Zero Trust and accelerate the enterprise journey to full cloud and multi-cloud. The infrastructure-agnostic platform deploys easily and seamlessly, enabling IT and security teams to:
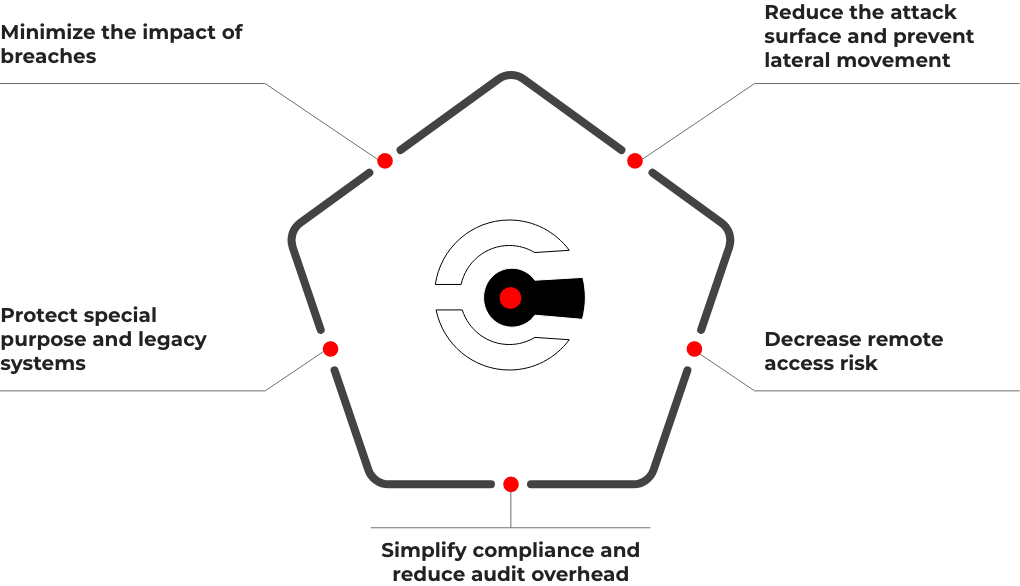
Comprehensive context of risk, intent, identity applied to each access request: user to app, app to app, and OT/device to application
Policies updated dynamically if context changes
Built in threat feed integrations and reputation feeds provide enhanced context to aid in policy decisions
Automated ML/AI based policy identification and recommendation engine to easily define and manage policies at scale
Skyview visualization for visual threat and policy impact analysis
Centralized policy management and access control
Dynamically isolates/stops breaches at workload and/or endpoint
Limits the blast radius for new attack vectors/unknown threats
Automatically restricts access based on trust model
Auto-quarantines compromised devices
Is based on Zero Trust Architecture to block and prevent the spread of advanced threats in hybrid networks
Extends Zero Trust protection from users and endpoints to crown jewels, via a comprehensive, context-rich approach to threat prevention
Deploys seamlessly, with no business disruption during deployment and installation, and no changes to network infrastructure
Future-proofs the network for secure cloud migration and adoption of multi-cloud
Provide direct, secure remote user access to corporate applications without requiring a VPN
Granular role-based policies based on least privilege access
Applications never exposed, invisible to bad actors and unauthorized users
Broad support for applications in public cloud and data center
Protect sensitive assets (crown jewels) and prevent lateral movement with Zero Trust segmentation
Allow access only from known and verified users, devices, and applications in sanctioned locations
Enable dynamic policies that adapt to changes in trust posture
Protect endpoints with dynamic whitelisting/allowlisting
Include all devices such as laptops, POS, OT and legacy systems
Enforce security with quarantine templates
Server/device lockdown and process control
Discover all devices and assets in the network
Eliminate blind spots
Visualize suspicious or malicious traffic
Simulate policy behavior
Learn More
By submitting this form, you agree to ColorTokens
Terms of Service and
Privacy Policy