 Become a Partner
Already a partner ? Login
Become a Partner
Already a partner ? Login
Program
Partner Program Overview
Designed to deliver unparalleled customer value and accelerated mutual growth by harnessing partner expertise and ColorTokens cybersecurity technology.
Learn MoreInfrastructure
Quick Links
Case Study
Industry Solutions
Quick Links
Program
Designed to deliver unparalleled customer value and accelerated mutual growth by harnessing partner expertise and ColorTokens cybersecurity technology.
Learn MoreFeatured Topic
Newsletter

Leading organizations across industries depend on legal, professional services, and consulting firms for best practices and superior business outcomes. Often these service companies see a wide range of confidential client data, including key intellectual property and strategies. Threat actors view them as targets, and even as entry points to their client businesses.
As analytics, technology, and online services become integral to business models, the sensitive information that companies possess becomes more vulnerable to exposure. Even a single data breach could cause devastating financial and reputational damage.
Data protection and strong security postures are integral to legal and other professional services that work with private and proprietary information. ColorTokens’ zero trust approach provides best-in-class cybersecurity solutions that allow law firms and other professional services to be more cyber resilient and to lead their industries in implementing modern, proactive security solutions.
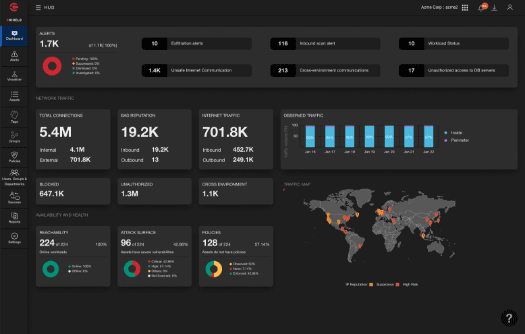
Take ColorTokens Xshield for a test drive.
See HowRise in sophisticated cyberthreats to steal confidential data
Loss of billable hours and clientele due to unscheduled downtime
Growing insider threat risk from employees mistakenly or maliciously causing data breaches
Increasing compliance requirements from regulatory authorities
Ever-expanding attack surfaces, including mobile devices, cloud data storage, and legacy systems
Potential security vulnerabilities associated with client onboarding and offboarding
Assess security posture in real-time and gain awareness of suspicious traffic patterns between users and workloads hosting sensitive client data. Implement a zero trust approach to secure every application based on value, risk, and attack surface.


Enable micro-segmentation within and across bare metal or hybrid-cloud environments and isolate critical assets. Limit the attack surface by granting access purely based on a user’s role and authority.
Gain granular visibility and lock down endpoints, such as laptops and desktops, making them tamper resistant to known and unknown threats like malware, ransomware, and sophisticated lateral-moving advanced persistent threats.


Address compliance needs of many standards and frameworks, including CCPA, GDPR, and PCI-DSS. Avoid compliance violations and fines by isolating and controlling communication within, across, and to the segmented groups under audit.

Learn More
By submitting this form, you agree to ColorTokens
Terms of Service and
Privacy Policy