 Become a Partner
Already a partner ? Login
Become a Partner
Already a partner ? Login
Program
Partner Program Overview
Designed to deliver unparalleled customer value and accelerated mutual growth by harnessing partner expertise and ColorTokens cybersecurity technology.
Learn MoreInfrastructure
Quick Links
Case Study
Industry Solutions
Quick Links
Program
Designed to deliver unparalleled customer value and accelerated mutual growth by harnessing partner expertise and ColorTokens cybersecurity technology.
Learn MoreFeatured Topic
Newsletter
The ever-evolving cyber threat landscape necessitates continuous adaptation of security strategies. However, the presence of legacy devices within modern networks creates a complex challenge for vulnerability management. These outdated systems, which may still be executing critical business processes, are often lacking vendor support and security updates. This makes them prime targets for exploitation. CISOs face a constant struggle: balancing the need for innovative applications with the security risks associated with outdated platforms. This blog delves into two conundrums:
1. Legacy Applications on Modern Operating Systems (OS): Patches for the underlying OS are available, but the application itself may lack vendor support, leaving vulnerabilities unaddressed.
2. Modern Applications on Legacy OS: Patching the application might be impossible or infrequent, leaving the entire system susceptible to exploits.
Both scenarios raise concerns about OS vulnerabilities and vulnerabilities within the application itself. For example, a legacy HRM (Human Resource Management) application running on a modern OS – even with updated OS, the application’s inherent vulnerabilities remain. A study by Avanade revealed that, on average, 31% of technology within organisations is made up of legacy systems.
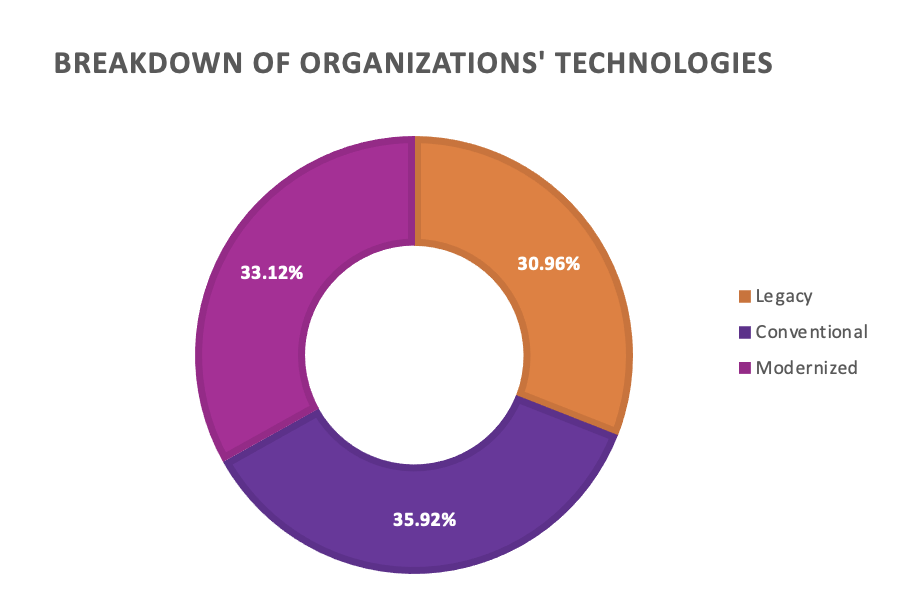
While standard Vulnerability Management techniques and solutions like patch management, vulnerability scanners, configuration management, and integration with SIEM (Security Information and Event Management) are essential tools for securing modern systems, they often face limitations when dealing with legacy devices, particularly those running on end-of-life (EOL) operating systems or applications. This is mainly due to the following reasons:
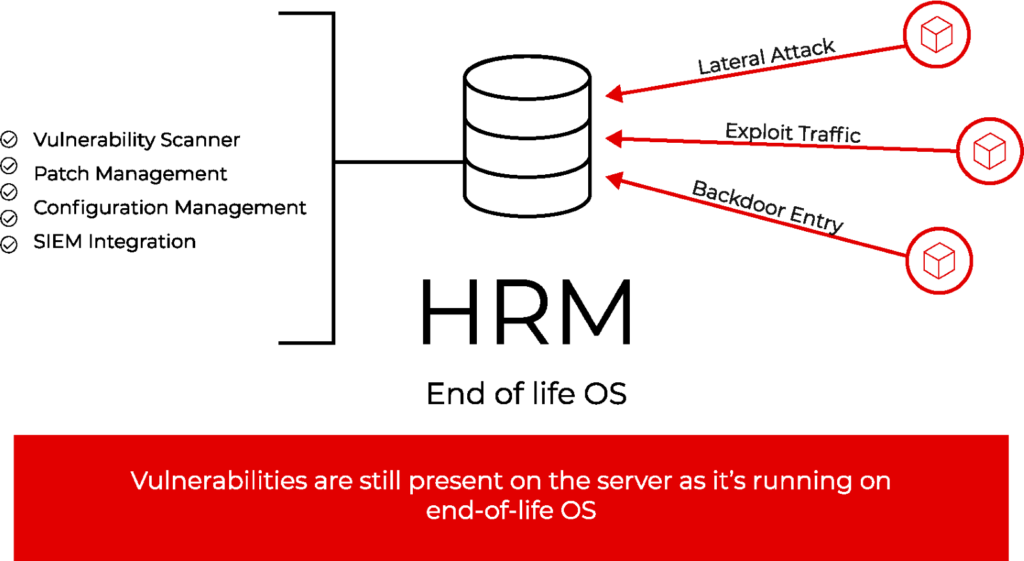
An HRM server running on EOL OS, with all the standard Vulnerability Management techniques in place is still vulnerable and can be breached by any adversary
So, how can these risks be mitigated?
Microsegmentation offers a more granular and dynamic approach to network security:
Benefits of using Microsegmentation for Legacy Devices:
Vulnerability Management for Legacy Devices with ColorTokens:
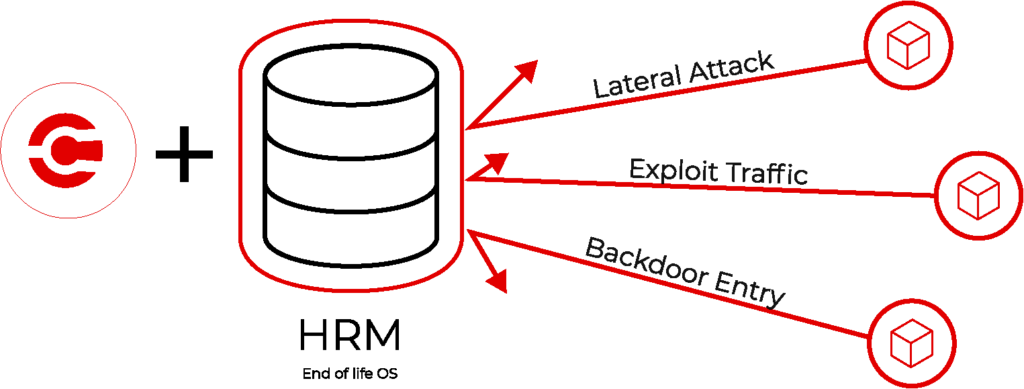
Microsegmentation with ColorTokens Gatekeeper secures Legacy system and prevents the network from being breached
ColorTokens’ Gatekeeper solution addresses the concerns of legacy devices by offering robust, agentless security specifically designed for these environments. By creating a secure, virtualized micro-perimeter around the legacy device, the Gatekeeper effectively isolates it from the rest of the network, significantly reducing the attack surface and preventing the lateral movement of potential threats. Additionally, the Gatekeeper’s ability to monitor and control network traffic to and from the legacy device enables real-time anomaly detection and automated mitigation measures, further enhancing security posture. This agentless approach eliminates the need for complex installations or modifications to the legacy system itself, making the Gatekeeper a user-friendly and efficient solution for securing these critical assets.
For more information, please contact us
By submitting this form, you agree to ColorTokens
Terms of Service and
Privacy Policy