 Become a Partner
Already a partner ? Login
Become a Partner
Already a partner ? Login
Program
Partner Program Overview
Designed to deliver unparalleled customer value and accelerated mutual growth by harnessing partner expertise and ColorTokens cybersecurity technology.
Learn MoreInfrastructure
Quick Links
Case Study
Industry Solutions
Quick Links
Program
Designed to deliver unparalleled customer value and accelerated mutual growth by harnessing partner expertise and ColorTokens cybersecurity technology.
Learn MoreFeatured Topic
Newsletter
In my blog on the new Xshield update, I mentioned four new capabilities driven by our extensive experience implementing microsegmentation projects. Let’s dive deeper into risk measurement and discuss its importance.
You may wonder why we incorporated risk measurement into a microsegmentation solution. After all, isn’t the goal of microsegmentation to reduce enterprise risk by implementing the principles of least privilege?
The issue is that most enterprise networks are designed to maximize collaboration and productivity. They are almost always flat and allow open communication between workloads and endpoints. Implementing least-privilege principles is like the paradox of an unstoppable force meeting an immovable object!

We can say with certainty that implementing least-privilege access accurately will be a lengthy and expensive endeavor for most enterprises. It could also be argued that this may be beyond the acceptable risk level for most enterprises and, therefore, difficult to secure budgets for. So, you see that measuring risk is essential while implementing microsegmentation; it helps determine your milestones.
Implementing microsegmentation is usually an infrastructure-wide project and involves several stakeholders. The security organization generally drives it but requires active participation by information technology personnel and application owners. So, we have many stakeholders in this project. Every project needs a plan, so we define goals, success metrics, milestones, etc. If your use case for microsegmentation is application ring-fencing, then your project plan may look like this:
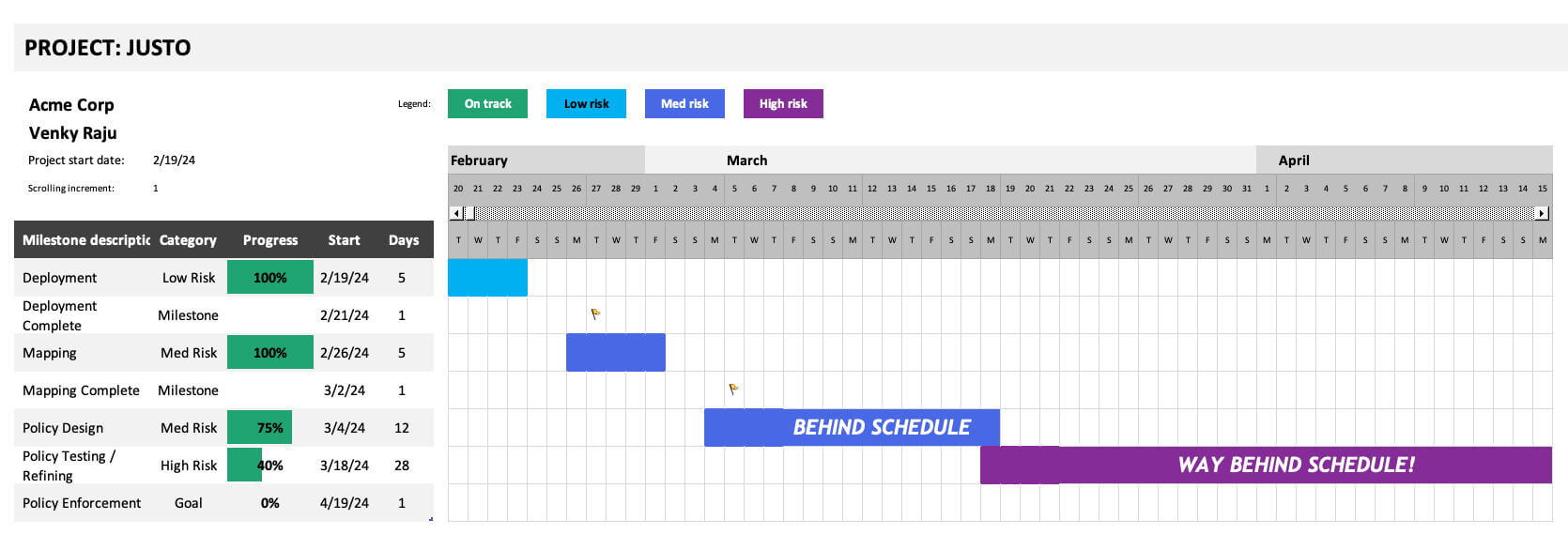
The early milestones, like deployment and mapping, are relatively easy to track. But as we move into policy design, testing, and refinement, the difficulty in measuring the risk reduction makes tracking difficult. This brings us to the first and perhaps most important reason why risk measurement is critical. Stakeholders get weary as the weeks go by, and project managers cannot provide an accurate state of the project. In speaking with enterprises that attempted microsegmentation previously, this has been the primary cause of the project being shelved. The alternative could be worse if microsegmentation were mandated by compliance requirements or other risk factors; you’re in for a death march!
Microsegmentation is often implemented as part of the enterprise’s Zero Trust initiatives. Forrester’s David Holmes writes, “Quick (and broadly visible) wins are important in a long security project if for no other reason than to keep the budget coming. Microsegmentation projects require mindfulness and discipline, and when executed properly, no one notices when [they’re] working.”
What better way to achieve quick wins than adopting the Pareto principle? We accomplish a large part of the overall goal if we can mitigate 80% of our risk with 20% of the effort. This can also create a halo effect and encourage application owners to participate actively in the project. How do we figure out what 80% of the risk is? We need a way to measure it! So this is reason #2 for risk measurement.
In an era of ever-increasing sophistication, attackers still prefer the path of least resistance. After all, the longer the attacker stays in the network, the more vulnerable they become to detection. From a microsegmentation point of view, the low-hanging fruit for attackers are systems with ports exposed to the public Internet, unnecessary open ports (LLMNR and NetBIOS, for example), wide open management ports (SSH, RDP, WinRM, etc.), among others. Hosts running end-of-life software, including operating systems like Windows XP, Windows 2003, etc., are especially vulnerable.
Measuring and quantifying these risks is essential so that the microsegmentation policies address these risks at the highest priority.
The new Xshield update introduces microsegmentation risk as a first-class attribute. We quantify every asset’s attack surface and blast radius and compute an overall risk score. This is then used to determine the aggregated risk score for any group of assets. For example, we can compute the risk of an environment, an application, a facility, etc. The attack surface and blast radius are calculated using a proprietary algorithm that considers the number of listening ports, the sources of incoming traffic, destinations accessed, the protocols employed, etc.
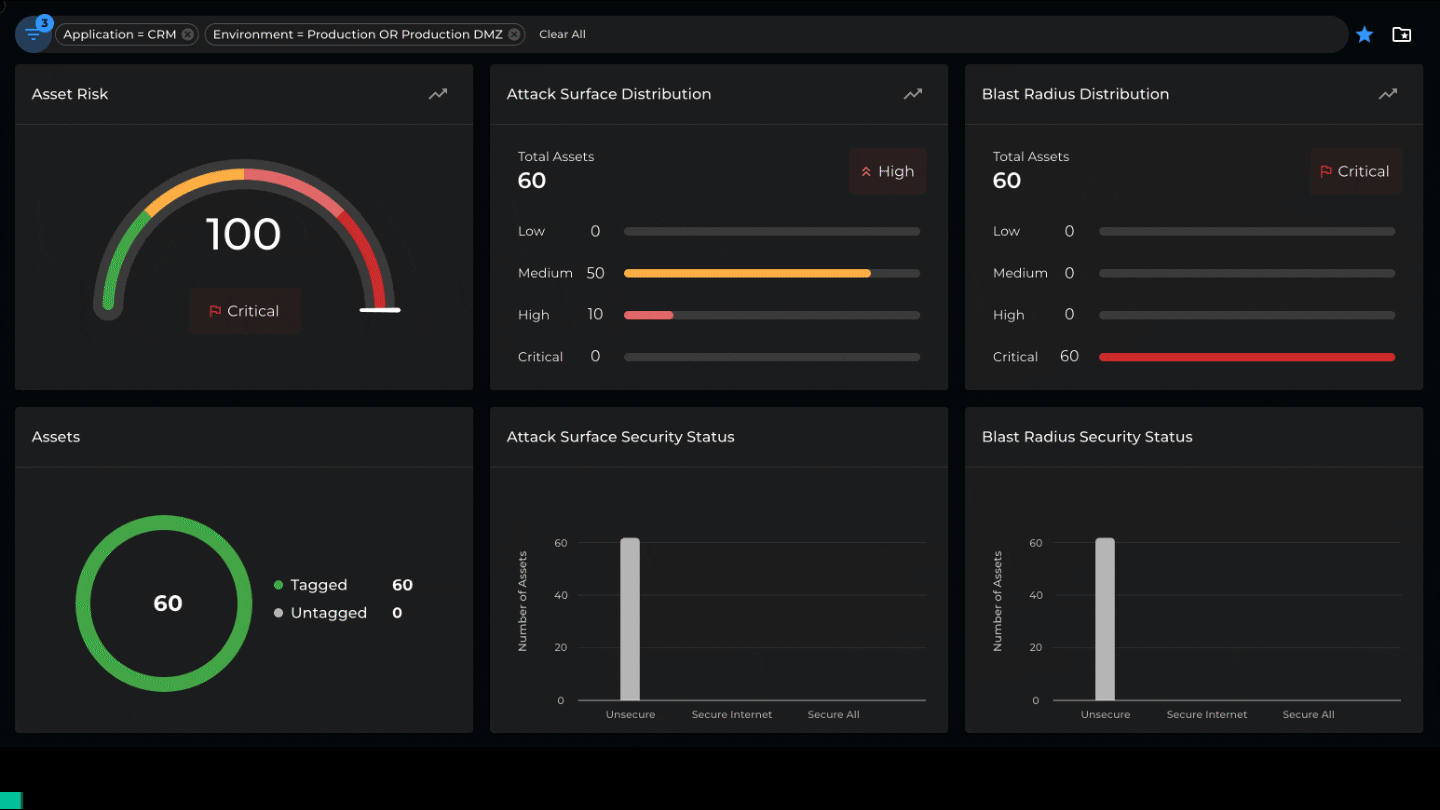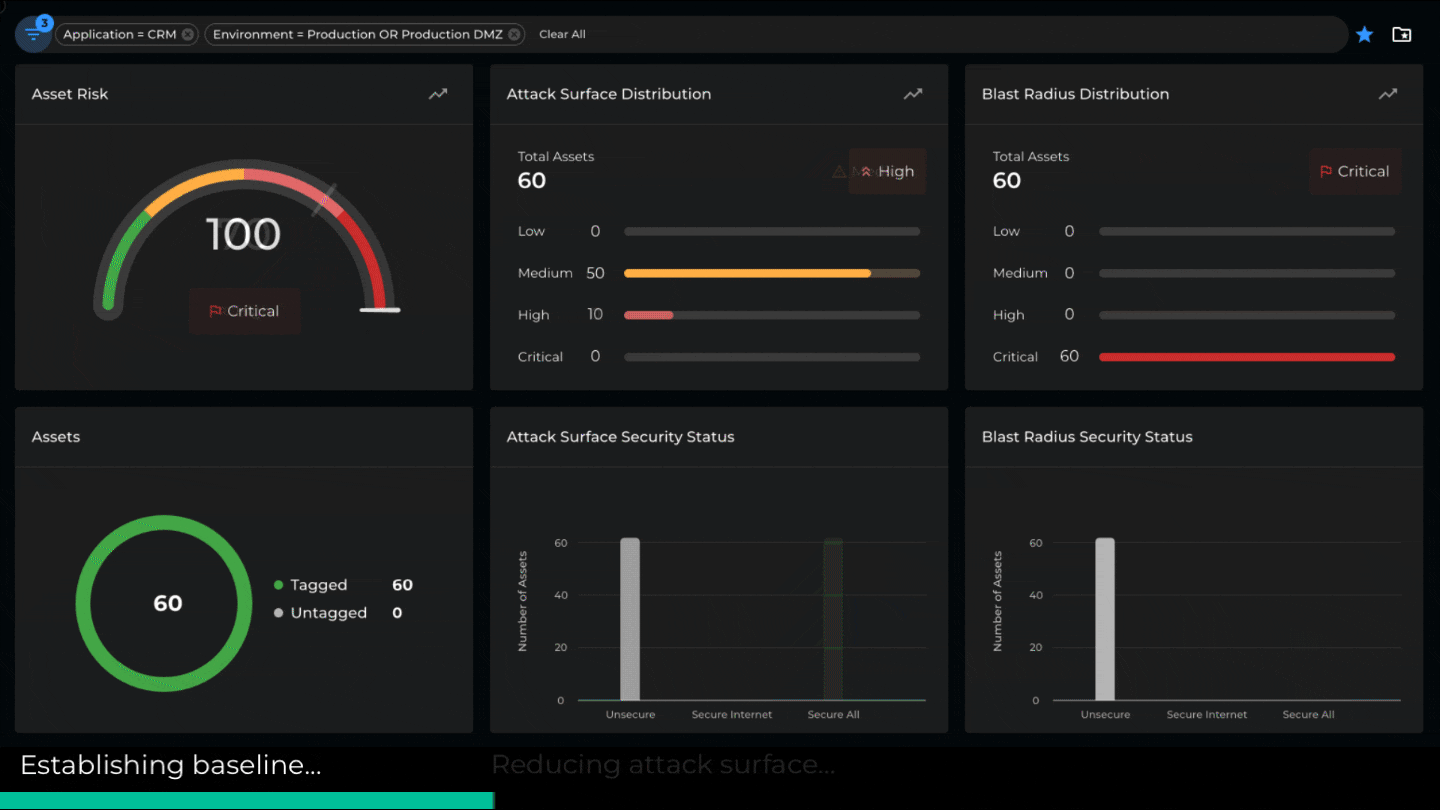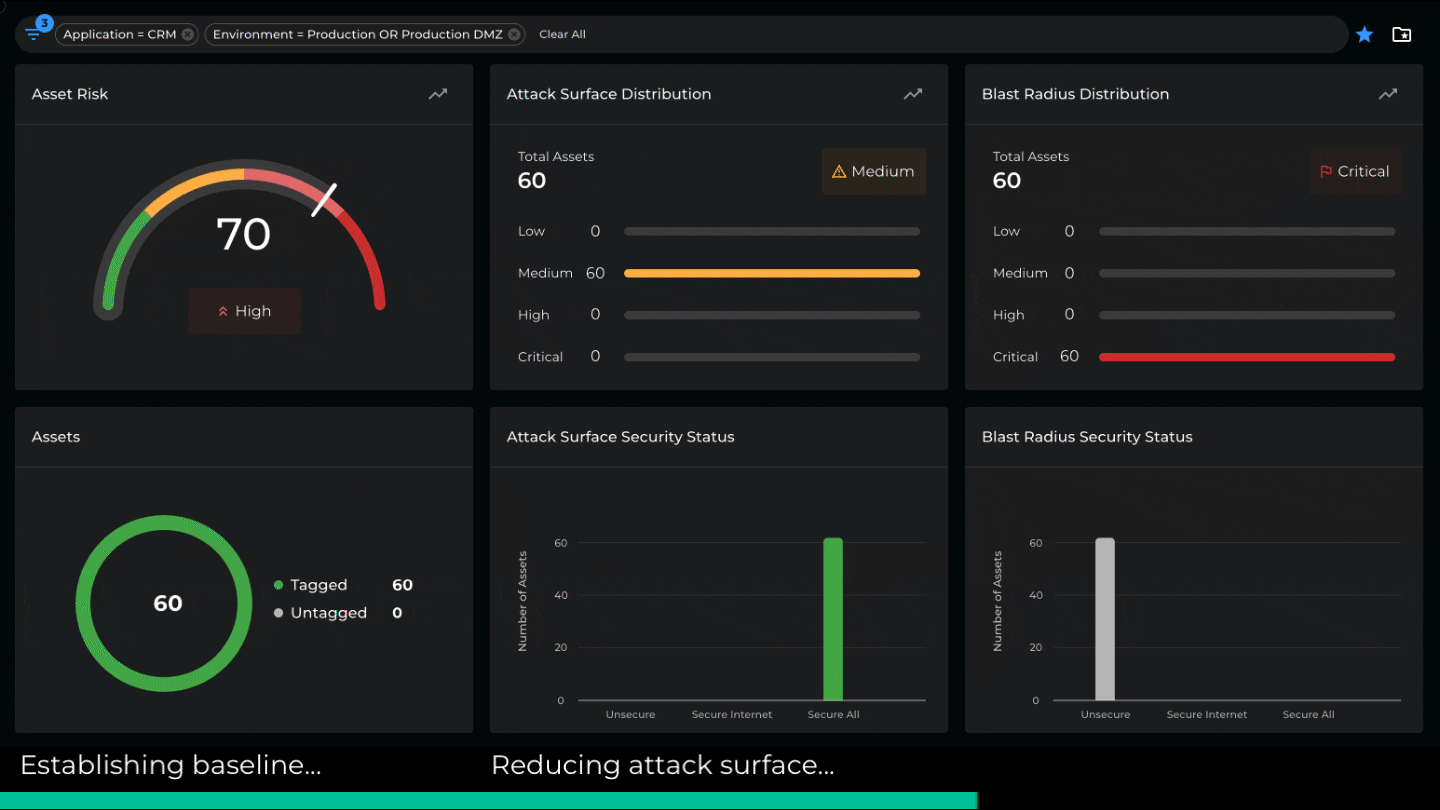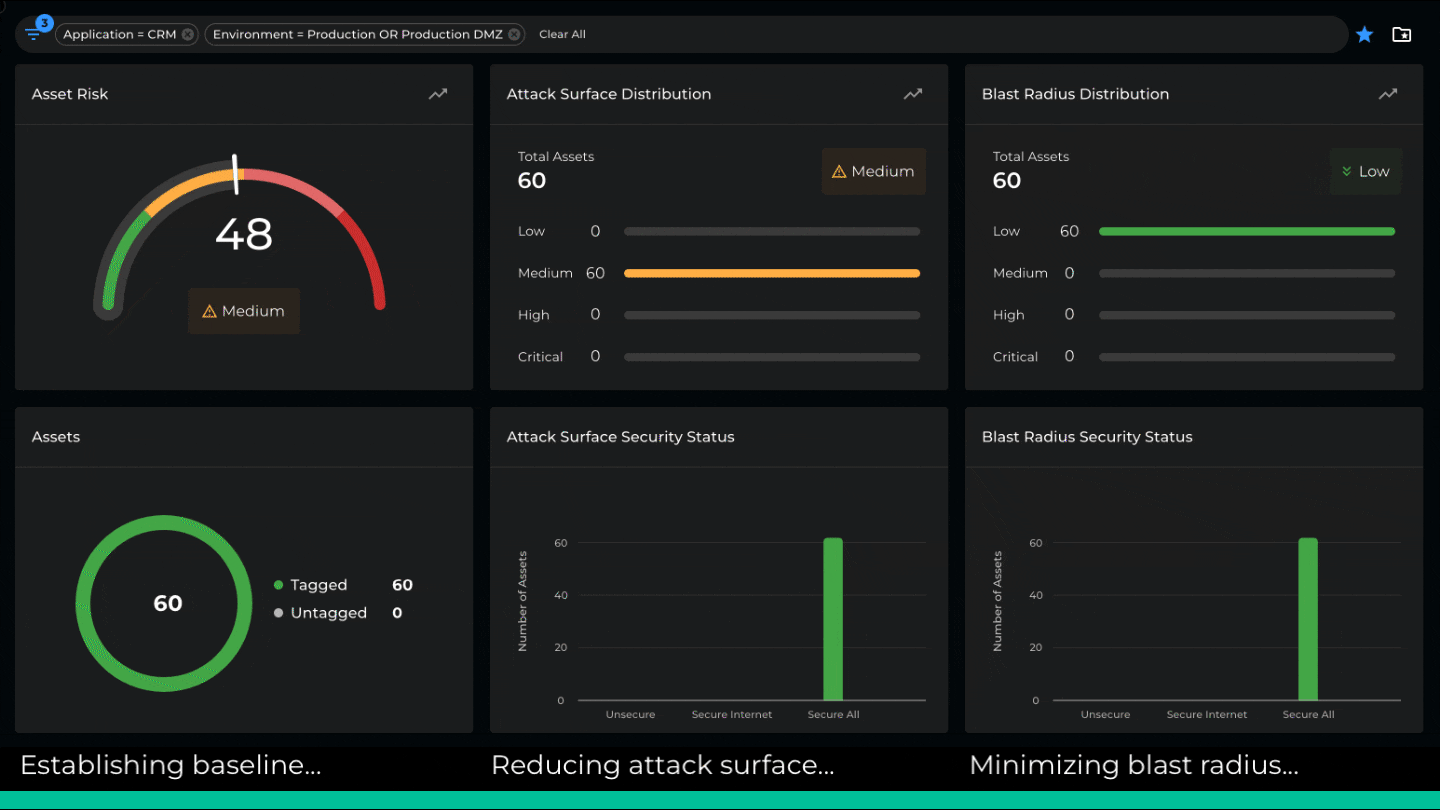
Understanding the distribution of asset risk within a location or environment can help identify quick wins and prioritize individual applications or asset groups for microsegmentation. Additionally, real-time risk measurements help project managers track the project’s progress and deliver clear and practical metrics to stakeholders.
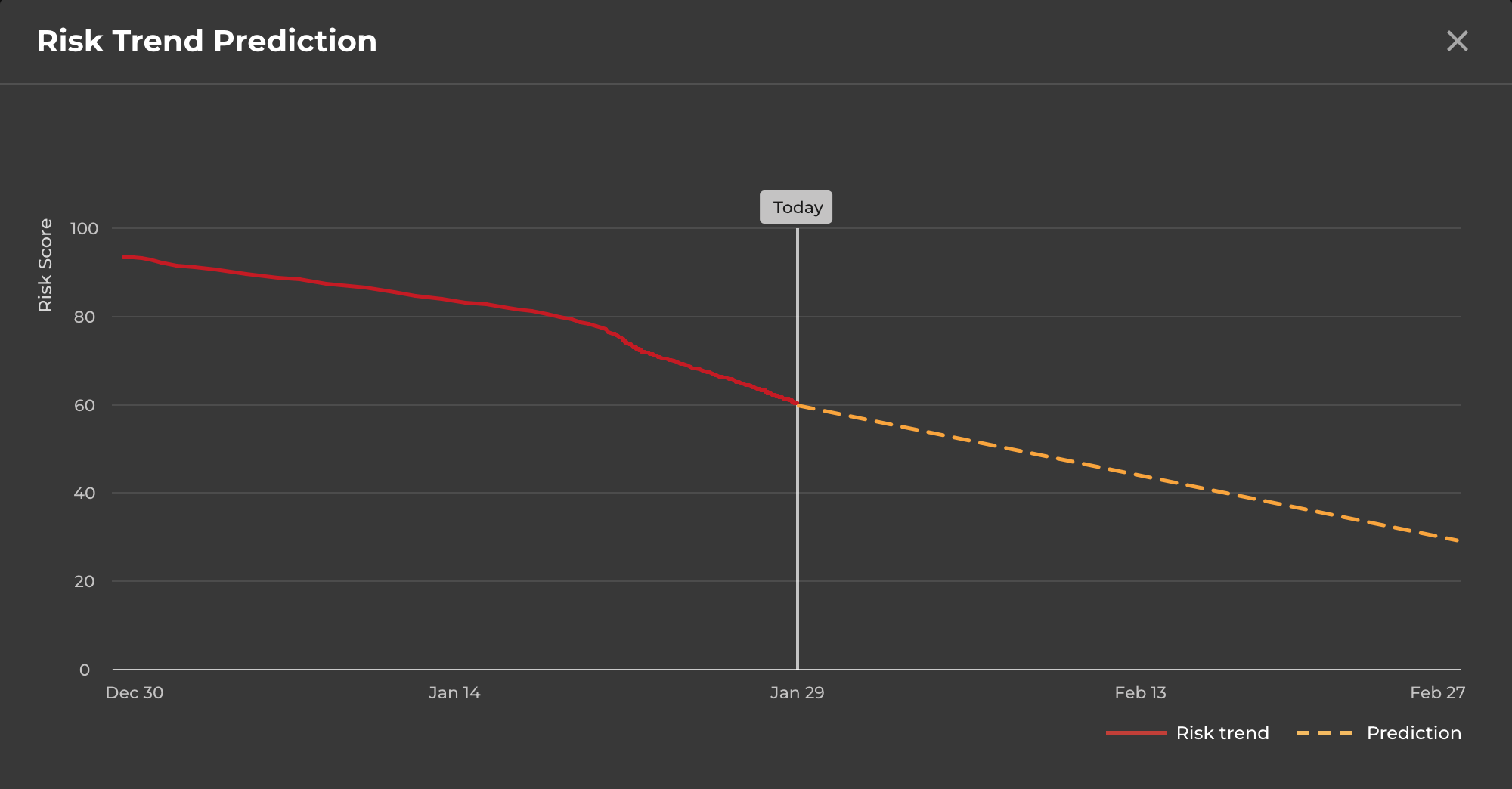
We are genuinely excited about how this capability can help you mitigate one of the biggest challenges of large-scale microsegmentation projects. For more information or a live demonstration of this capability, please get in touch with us.
By submitting this form, you agree to ColorTokens
Terms of Service and
Privacy Policy