 Become a Partner
Already a partner ? Login
Become a Partner
Already a partner ? Login
Program
Partner Program Overview
Designed to deliver unparalleled customer value and accelerated mutual growth by harnessing partner expertise and ColorTokens cybersecurity technology.
Learn MoreInfrastructure
Quick Links
Case Study
Industry Solutions
Quick Links
Program
Designed to deliver unparalleled customer value and accelerated mutual growth by harnessing partner expertise and ColorTokens cybersecurity technology.
Learn MoreFeatured Topic
Newsletter

Elimination of air-gapped security and the IoT proliferation to cut down manpower and operational costs and improve efficiency have exposed critical infrastructures to cybercriminals. The energy sector, Dams, Defense services, Airports etc. rely heavily on technology and automation for access controls, surveillance, staff management, ticketing, check-ins, and personnel authentication to streamline operations.
Possession of sensitive data, control of critical functions, and regular interaction with third-party vendors make the cybersecurity landscape quite complex for these entities. Any single instance of a cyberattack on a country’s critical infrastructure can have widespread consequences beyond financial and reputational loss.
ColorTokens provides a unified and platform-agnostic security solution that will scale along with the rapidly changing digitization projects while reducing operational complexity. ColorTokens’ Xtended ZeroTrust™ Platform empowers a country’s critical infrastructure to stay a step ahead of emerging cyber risks.
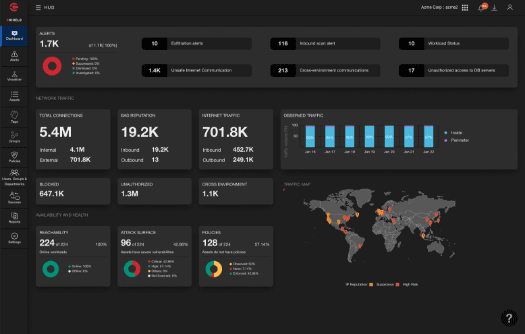
Take ColorTokens Xshield for a test drive.
See HowArchitectural silos due to multiple security solutions decrease operational efficiency
Risk of vendor and third-party introduced vulnerabilities
Advanced persistent threats (APTs) that move laterally across networks
Need for agile security architecture to protect hybrid, multi-cloud environment, third party integrations as well as traditional on-premises services
Undetected insider attacks and information leakage that lead to monetary loss, regulatory actions, and business disruption
Absence of trained security professionals and expertise to help strengthen security posture
Monitor authorized and unauthorized traffic across the infrastructure’s applications, servers, workloads, and endpoints on-premise as well as on the cloud in any multi-vendor data center environment. Get a centralized view on one comprehensive, web-based dashboard, instead of juggling multiple monitoring tools.


Reduce the attack surface by implementing zero trust security policy. Separate transactional, applications, and user database environments through software-defined micro-segmentation and ensure that access to these applications is allowed only after authentication.
Prevent lateral movements with fully customizable lockdown capabilities. Make check-in kiosks, ticketing systems, building, and video management systems, and operational control centers tamper-resistant to known and unknown threats by enabling process-level visibility and permitting only the known-good (or whitelisted) processes to run.


Reduce operational complexity with a unified security solution. Avoid collating and analyzing alerts from multiple security tools. Enable security and risk teams with a holistic security solution that automatically applies micro-segmentation policies on critical applications and enforces zero trust access to third-party users.
Learn More
By submitting this form, you agree to ColorTokens
Terms of Service and
Privacy Policy