 Become a Partner
Already a partner ? Login
Become a Partner
Already a partner ? Login
Program
Partner Program Overview
Designed to deliver unparalleled customer value and accelerated mutual growth by harnessing partner expertise and ColorTokens cybersecurity technology.
Learn MoreInfrastructure
Quick Links
Case Study
Industry Solutions
Quick Links
Program
Designed to deliver unparalleled customer value and accelerated mutual growth by harnessing partner expertise and ColorTokens cybersecurity technology.
Learn MoreFeatured Topic
Newsletter
Microsegmentation has emerged as an effective security strategy against sophisticated threats faced by businesses today. It protects workloads, both in the data center and cloud, by creating smaller secure zones that are isolated from each other. These smaller security zones reduce exposure and attack surface drastically. While segmentation of workloads and applications is the first step, the real challenge faced by security professionals is the orchestration and implementation of policies with minimum disruption to the traffic flow.
Policy enforcement could be via host-based distributed firewalls or traditional firewalls, but the ease of deployment and administration can be an uphill climb without an effective policy engine. A sophisticated policy engine that gives more flexibility in policy administration and performs most of the policy decisions by itself will go a long way in making your microsegmentation journey successful. It brings down the number of security alerts and, in turn, reduces operational expenses and results in a happier security operations team.
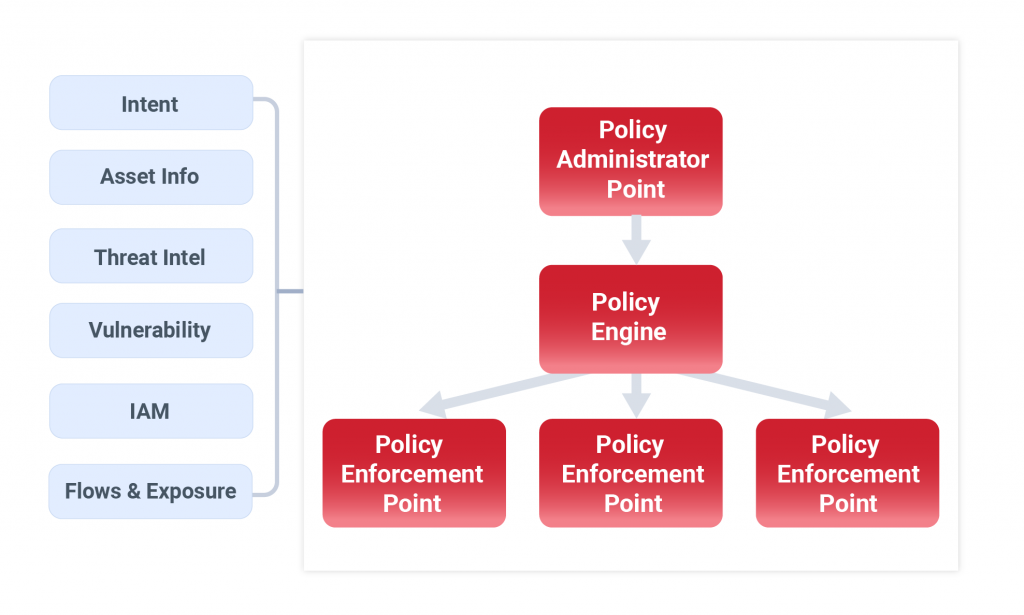
Flexibility in defining segments using a variety of attributes; they could be workload tags, e.g. environment, application, or location; attributes e.g. subnet, geo-location; or system attributes e.g. OS, OS versions with a patch, vendor, or mix of these attributes. Without such flexibility, defining segments as per business and security needs will be impossible and will hamper rollout.
Policy dynamics must follow attributed based segment definition. The policy engine should continuously listen to changes in assets, its tags, location, addresses, etc. and recompute policies. E.g. If a segment is defined using subnet, new workloads joining that subnet should automatically get required policies. Changes like workload relocation or repurpose should be handled seamlessly to avoid unwanted gaps in security.
Policies should adapt to change in environment and threat level, e.g. on detecting a critical threat on a workload, the policy engine should quarantine the infected workload. The policy engine should continuously assess the change and adapt policies accordingly. Adaptive policies should be configurable and intent-driven.
The aim of any microsegmentation project should be to reduce the attack surface to a minimum and controlling traffic flow to these segments with fine-grained policies that ensure authorized access only. While it is OK to start with macro or coarse segments, the policy engine should provide a path to craft granular segments without disruption.
A good policy engine should be able to learn and suggest segments along with policies for the segments. It could be in the form of application dependency maps or simply segmentation policies; the engine should recommend a full set of policies including infrastructure, e.g. DNS, Active Directory, as well as NOC/admin access policies e.g. SSH, RDP. Such features may not be desirable for small deployments, but large scale deployments can benefit from policy recommendations across segments.
Enforcement of new policies could disrupt traffic and result in unintended downtime. To avoid this, the policy engine must provide workflows to validate policies before enforcement. This is a must to ensure that there is no business disruption while rolling out segmentation in the production environment. Similarly, the policy engine should also have the ability to enforce policies on selected segments at a time, not all segments at once. This gives security teams an opportunity to monitor the segment below large scale enforcement.
The business landscape is dynamic. Expansions and acquisitions will require the security infrastructure to scale and adapt to the new business needs. The same holds true for the policy engine too. It should be capable of scaling to the current and forecasted workloads across hybrid cloud environments.
Cloud adoption and migration have become imperative for businesses to grow. The policy engine must work with cloud-native interfaces where enforcement methods may vary depending on the cloud vendor. It should be able to handle elastic workloads and should reconfigure policies as VMs join or leave the application. Also, the policy engine should work with hybrid-cloud applications and provide a path to migrate the application to cloud and vice-versa without changing policies.
Along with the ability to backup, restore, and rollback, change of approval workflows driven by traditional commit is also desirable. Schedule based policies can be applied to contractor and vendor access. This eliminates policy bloat by removing unnecessary policies that are no longer required.
Though this may not be a feature you can’t do without, for certain specific use cases, peer authentication and encryption may be required. Understand the capabilities of the policy engine as well as policy enforcement points to check whether the solution can encrypt certain selected inter-segment flows.
Policy creation and implementation is an ongoing process and it may take some time for your security teams to fine-tune the policy engine. To ensure this, there must be enough hooks to trace every allowed or denied flow to the matching policy. This is a very important tool for debugging issues in a live production environment.
Security frameworks like Gartner CARTA, SASE, NIST Zero Trust Architecture acknowledge the role of policy engine as the fulcrum of future security management. An efficient and automated policy engine simplifies your microsegmentation journey and allows you to implement granular security on a larger scale. If you’re on the lookout for a microsegmentation solution, evaluate the microsegmentation policy engine on the parameters that suit your organizational and business needs. A well-designed policy engine should include high-level automation which significantly reduces security ops resources and simplifies security in the process.
ColorTokens Xshield provides unmatched deep visibility along with a powerful policy engine that serves complex organizational needs. Policy administration workflows simplify data center and cloud segmentation workflows in a single pane of glass, from visualizing to segmenting and thereafter monitoring to responding.
By submitting this form, you agree to ColorTokens
Terms of Service and
Privacy Policy