 Become a Partner
Already a partner ? Login
Become a Partner
Already a partner ? Login
Program
Partner Program Overview
Designed to deliver unparalleled customer value and accelerated mutual growth by harnessing partner expertise and ColorTokens cybersecurity technology.
Learn MoreInfrastructure
Quick Links
Case Study
Industry Solutions
Quick Links
Program
Designed to deliver unparalleled customer value and accelerated mutual growth by harnessing partner expertise and ColorTokens cybersecurity technology.
Learn MoreFeatured Topic
Newsletter
As enterprises improve their security posture with microsegmentation, one gaping hole is unfettered access of users to their micro-segmented and protected workloads. The current state of the microsegmentation technology has no awareness of users and their roles or their business needs. Here’s how this gaping hole can be sealed with CTSP 1.2.
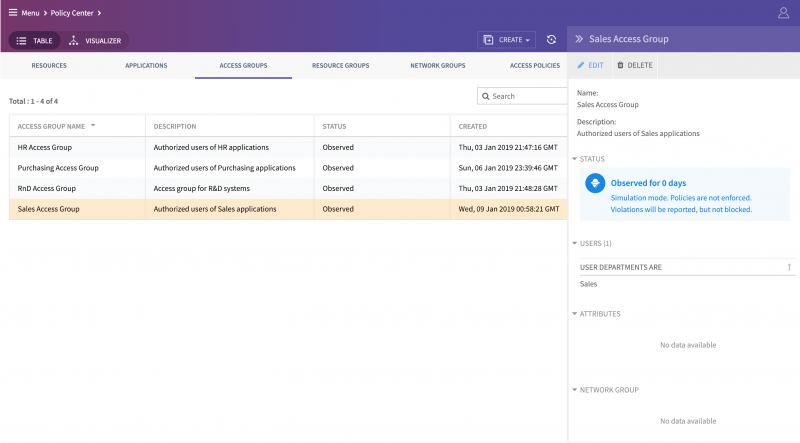
CTSP 1.2 integrates with enterprise user directory with both LDAP and SAML, and allows the creation of user “access groups” based on the user role, their department in the organization, the OS (Windows, OSX versions) they use, and the devices (HP, Apple, Dell, etc.) they prefer. Besides, one can also use the network, location and other tags to create groups.
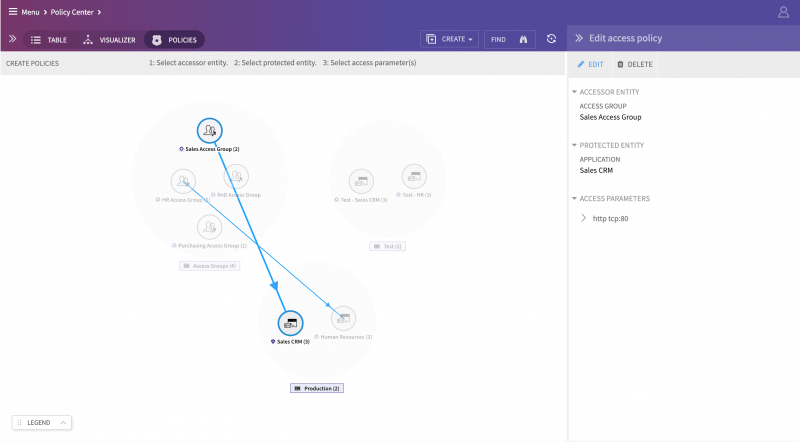
This allows controlling access to particular “Amazon VPC Linux servers” micro-segment via SSH to only users in the IT department and authorized as UNIX administrators while they are in office and using company-issued Windows 10 Lenovo laptops.
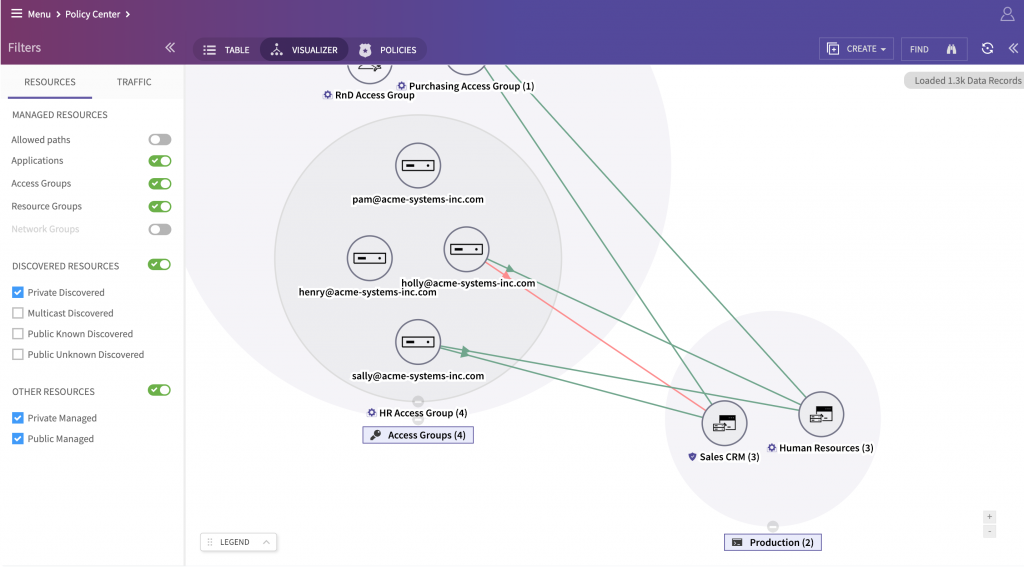
At the same time, the sales department users, using their MacBook Airs with latest Mojave can access the “Sales CRM segment” via the secure web to upload their most recent blog posts. Having such granular and flexible control is necessary to keep the business running and secure at the same time.
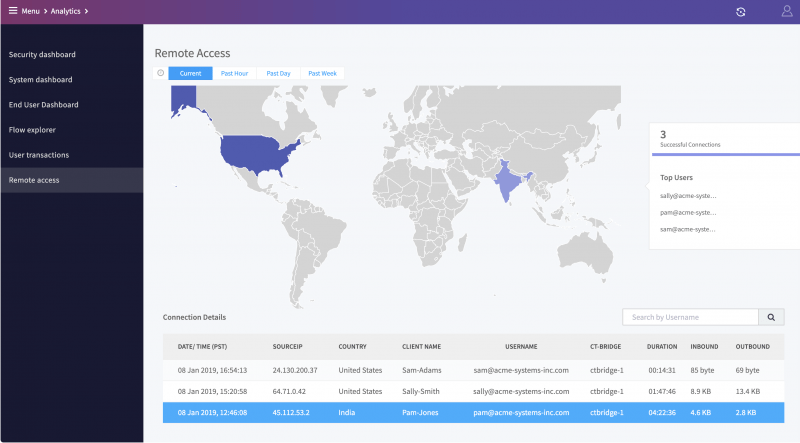
CTSP 1.2 now allows the authorized user to access protected micro-segments across the Internet with secure IPSec protected access without any VPN-like painful authentication on every corporate access. The remote access works with full certificate-based secure IPSec with no user intervention and is controlled to only authorized micro-segments with ColorTokens virtual enforcement appliance. This allows controlling access of not just employees but also third parties such as contractors, suppliers, vendors to remotely access only those applications and segments they need to do their work.
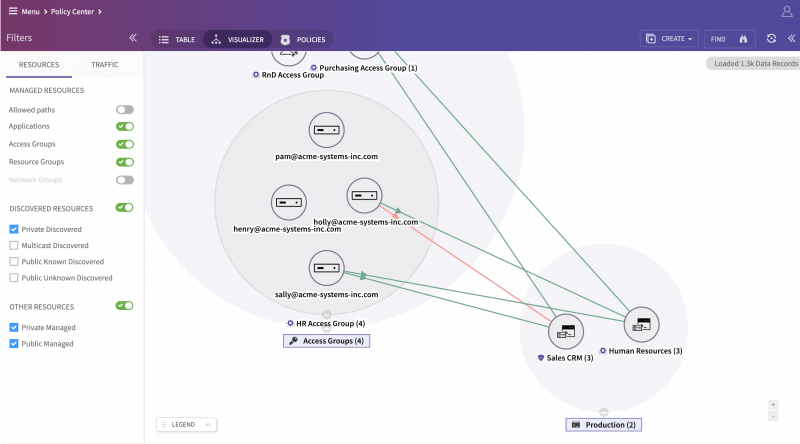
Security analysts know hunting and investigation have become key to maintaining the security posture. CTSP 1.2 now allows “Flow Explorer” to be either queried by visual searches or by expert queries comprising of tags, ports, protocols or attribute-based groups. This can be now used to narrow down to individual 5-tuple “Flow” record that is suspicious, unauthorized or just an outlier.
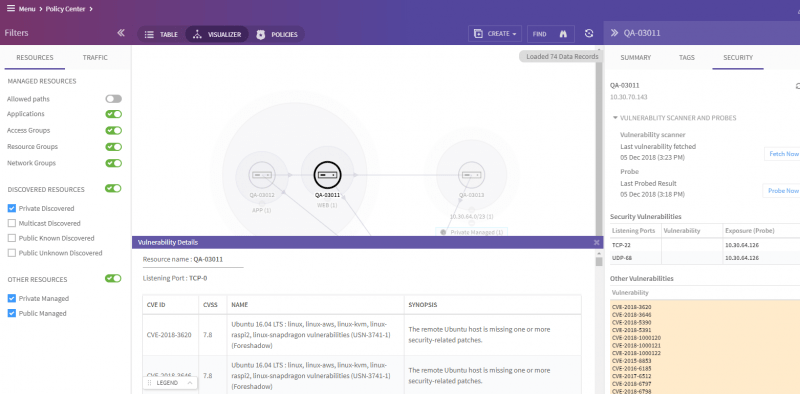
Every resource now has an expanded security tab which shows the vulnerabilities tied to the open ports and the reachability of these ports from different segments. The severity and details of each vulnerability can also be further explored. This allows security analysts to understand the true “breachability” of each resource and where they need to spend time tightening the security posture with policies, patching or other countermeasures.
There are many other nuanced features and functionality-improving experience and security of our customers. Here’s a sneak peek:
[fusion_youtube id=”iv1UWLwjl9c” alignment=”center” width=”500″ height=”300″ autoplay=”false” api_params=”&rel=0″ hide_on_mobile=”small-visibility,medium-visibility,large-visibility” class=”” css_id=””][/fusion_youtube]
Here’s more information on how ColorTokens can help protect your company from cyber threats.
By submitting this form, you agree to ColorTokens
Terms of Service and
Privacy Policy