 Become a Partner
Already a partner ? Login
Become a Partner
Already a partner ? Login
Program
Partner Program Overview
Designed to deliver unparalleled customer value and accelerated mutual growth by harnessing partner expertise and ColorTokens cybersecurity technology.
Learn MoreInfrastructure
Quick Links
Case Study
Industry Solutions
Quick Links
Program
Designed to deliver unparalleled customer value and accelerated mutual growth by harnessing partner expertise and ColorTokens cybersecurity technology.
Learn MoreFeatured Topic
Newsletter
During the stressful COVID-19 pandemic, governments are urging people to stay home. So, many people have adopted new ways to not only run their day-to-day lives, but also to make sure they are fulfilling. Zoom keeps millions of people connected. TikTok provides a creative outlet to escape shelter-in-place boredom. And Amazon is selling everything from N95 masks to those special I-need-this-in-my-life items.
In fact, practicing retail therapy to escape the COVID blues appears to be a major trend in 2020. Amazon’s Prime Day shopping event in October kicked off the retail holiday shopping season early, more than one month in advance of Black Friday and Cyber Monday. Prime Day resulted in a near 60% year-over-year increase in revenue for the online retail giant’s third-party small and medium sellers alone. Although Amazon did not release Prime Day sales totals, the company did announce that marketplace sellers earned more than $3.5 billion during the Prime Day event.1
With record sales like this in play, and people needing some cheer more than ever, online retailers could have an unprecedented 2020 holiday shopping season. The National Retail Federation’s “2020 Consumer Holiday Survey” found that 60% of consumers say they plan to purchase holiday items online this year. Nearly all online shoppers surveyed (91%) plan to take advantage of free shipping, perhaps to avoid breaking quarantine.2 And consumers expect to spend $998 on average on items such as gifts, food, decorations, and other holiday-related purchases for themselves and their families.3
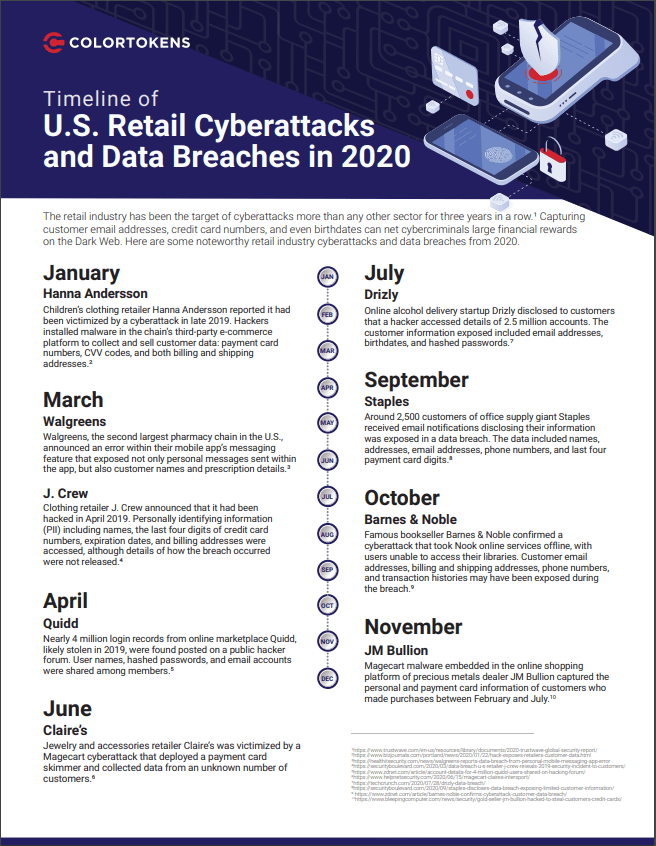
Cybercriminals have also noted the uptick in online shopping and are targeting retailers and online shopping sites. According to the 2020 Trustwave Global Security Report, the retail industry was the most-targeted sector for cyberattacks for the third year in a row, with nearly one-quarter of all attacks in retail.4 Apart from the vast jackpot of money generated within the online retail space, the sensitive personally identifying information (PII) required for most transactions is also attractive to cyberattackers. Names, addresses, birthdates, and credit card numbers can fetch high prices on the Dark Web or — even better for ransomware groups — might result in desperate retailers paying huge ransoms to mitigate data breaches.
In October, bookseller Barnes & Noble reported that it had been the victim of “unauthorized and unlawful access to certain Barnes & Noble corporate systems.” Later details revealed that customer PII — such as emails, phone numbers, and billing and shipping addresses — may have been exposed during the breach. The attack interrupted Nook-specific online functions as well as brick-and-mortar store transactions, when some point-of-sale (POS) cash registers were temporarily not functioning.5
Online shoppers store a lot of sensitive personal information on their favorite retail sites, so it’s important for online retailers to protect their customers’ private data and other PII. Here’s what online retailers can do to secure critical assets and become cyber resilient from Black Friday to Cyber Monday and all year-round.
Traditional security solutions don’t provide visibility into East-West server traffic. This makes it almost impossible to detect the presence of hackers once they’ve gained access to your network. An effective visibility solution will give you granular visibility and control over your network communications, including server traffic.
When you have complete cross-segment traffic visibility, any deviation in behavior can be detected and flagged by your security team. This information can be used to check and remediate systems or applications that have been attacked.
Another advantage of complete network visibility is that it simplifies PCI compliance. You can audit card-holder data environment (CDE) traffic to provide continuous validation of your PCI-DSS posture.
Cybercriminals are increasingly using phishing campaigns to bypass perimeter defense solutions. Your employees might click on a malicious email link thinking it’s from a trusted source. This would give the hacker the opportunity to install malware, spread laterally, and gain access to your servers, databases, and applications.
With software-defined microsegmentation, you can create logical segments coupled with intent-based resource access policies. These can span the hybrid infrastructure without requiring VLAN/ACLs or complex rules and configurations. Security policies can be driven down to application environments, users, and individual workloads, ensuring that access to applications is denied, unless explicitly allowed (in other words, zero trust).
In the event of an APT (Advanced Persistent Threat) or insider threat attack, you can isolate your CDE and critical database servers. The hackers can be blocked and isolated, drastically reducing the attack surface.
A company’s cybersecurity posture is only as strong as its weakest link, which is often an employee who hasn’t been educated on cyber hygiene best practices. You should train employees, vendors, and affiliates about security best practices. An informed workforce will be on its guard against phishing attacks and similar social engineering tactics used by hackers to exploit human psychology.
More rare — but not unheard of — are inside attackers. In September, e-commerce company Shopify reported that two rogue employees planned an inside job to steal transactional data.6 Tesla, the largest seller of electric vehicles (EVs) worldwide, avoided an inside threat this summer when an employee was offered $500,000 to deploy malware on the Tesla network that would allow a cybercriminal group to demand ransom. Fortunately, the worker reported the bribe to Tesla.7
With the holiday shopping season already in progress, online retailers need to ensure that their security solutions can defend their business against increasing malware threats and other cyberattacks. Adopting a proactive approach can reduce the attack surface and keep highly damaging data breaches at bay. Zero Trust Security can help you implement policies to ensure that access to data, applications, and workloads is limited to authorized users.
To find out more about how your online retail business can secure its data centers, applications, and endpoints, read ColorTokens’ Retail Security Solutions.
1 https://press.aboutamazon.com/news-releases/news-release-details/amazon-prime-day-2020-marked-two-biggest-days-ever-small-medium
2 National Retail Federation “2020 Consumer Holiday Survey,” October 2020.
3 https://nrf.com/insights/holiday-and-seasonal-trends/winter-holidays
4 https://www.trustwave.com/en-us/resources/library/documents/2020-trustwave-global-security-report/
5 https://www.zdnet.com/article/barnes-noble-confirms-cyberattack-customer-data-breach/
6 https://techcrunch.com/2020/09/23/shopify-data-merchant-breach/
7 https://www.wired.com/story/tesla-ransomware-insider-hack-attempt/
By submitting this form, you agree to ColorTokens
Terms of Service and
Privacy Policy