 Become a Partner
Already a partner ? Login
Become a Partner
Already a partner ? Login
Program
Partner Program Overview
Designed to deliver unparalleled customer value and accelerated mutual growth by harnessing partner expertise and ColorTokens cybersecurity technology.
Learn MoreInfrastructure
Quick Links
Case Study
Industry Solutions
Quick Links
Program
Designed to deliver unparalleled customer value and accelerated mutual growth by harnessing partner expertise and ColorTokens cybersecurity technology.
Learn MoreFeatured Topic
Newsletter
This article was first published on CSO Online Australia.
Businesses today rely heavily on greater connectedness to grow their customer base and expand their market share. To achieve this, enterprise networks should be capable of connecting with customers, partners, stakeholders, vendors, and third-party distributors across geographies via a variety of devices. This poses a serious security risk since it’s impossible to determine the intent of every single endpoint, machine, and application that is connecting to the network.
To counter this challenge, businesses are beginning to consider a ‘zero trust’ approach – trust no connection unless they have been explicitly allowed. The zero-trust security concept paves the way to proactively secure workloads, application environments, users and endpoints against internal and external threat actors. Though this is a fairly new concept for businesses that have relied mostly on perimeter security solutions, the dynamic landscape in which they operate today has many strong drivers for zero trust security adoption.
Applications are moving out of ‘secure’ private data centres and on to the cloud. The pace at which they are moving out is very rapid. According to the Right Scale State of the Cloud Survey 2017, a whopping 79% of company workload is run on the cloud, with 41 % on public cloud and 38% on private cloud.
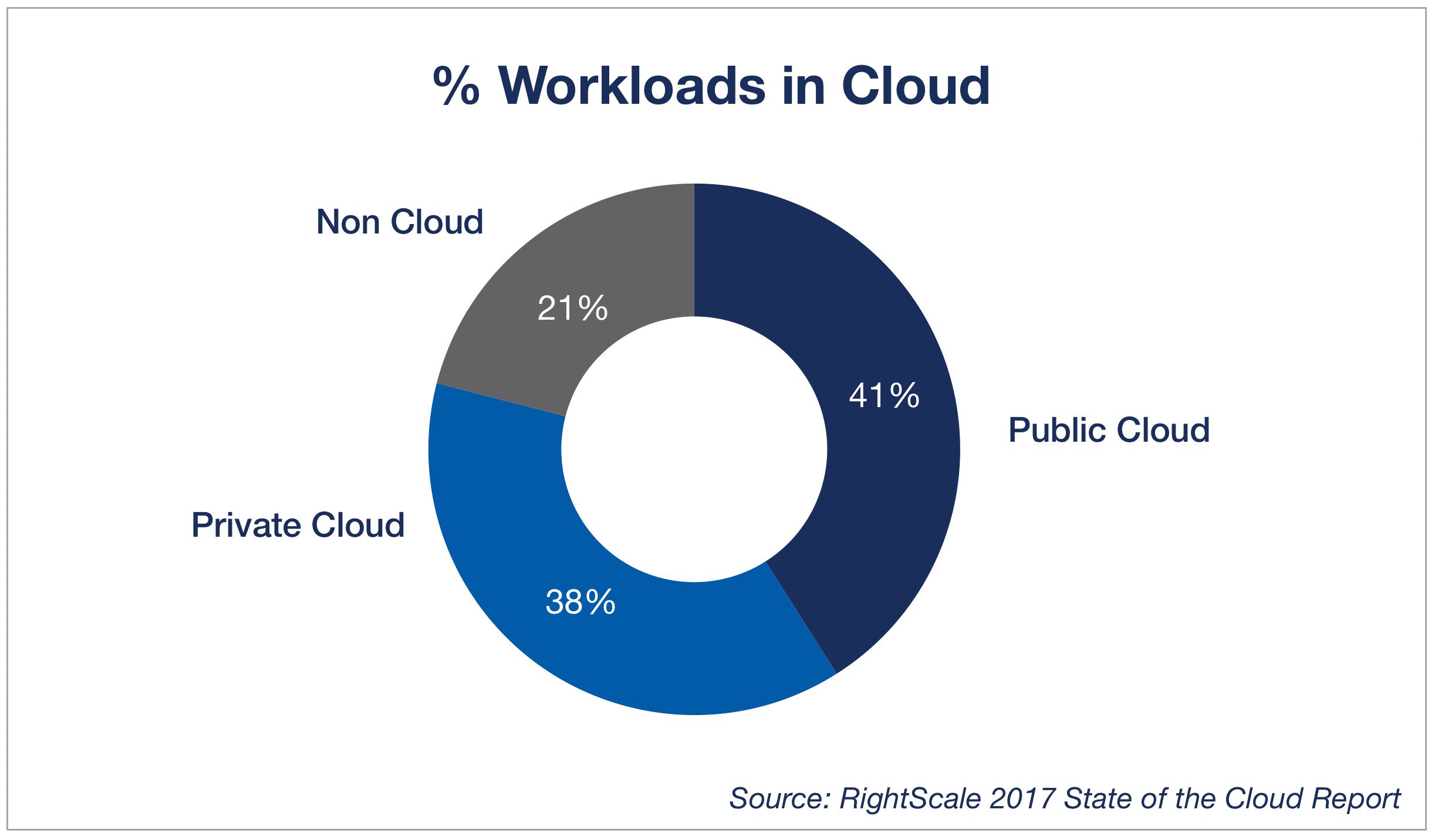
What does this mean for security? For starters, 41% of the workload is already outside the company’s secure perimeter. This means that apps, data, users, and devices are moving out of the enterprise’s fortifications, and securing them needs a new security paradigm. The old concept of trusting everything inside the perimeter, even assuming it was ever secure, suddenly becomes inapplicable because large portions of enterprise resources now reside outside the fortifications.
Here is where Zero Trust comes in. The rate at which resources are moving out to the cloud is one of the largest business drivers of zero trust.
By submitting this form, you agree to ColorTokens
Terms of Service and
Privacy Policy