 Become a Partner
Already a partner ? Login
Become a Partner
Already a partner ? Login
Program
Partner Program Overview
Designed to deliver unparalleled customer value and accelerated mutual growth by harnessing partner expertise and ColorTokens cybersecurity technology.
Learn MoreInfrastructure
Quick Links
Case Study
Industry Solutions
Quick Links
Program
Designed to deliver unparalleled customer value and accelerated mutual growth by harnessing partner expertise and ColorTokens cybersecurity technology.
Learn MoreFeatured Topic
Newsletter
Enables secure user access to applications and segments, vastly minimizes the attack surface and eliminates lateral movement
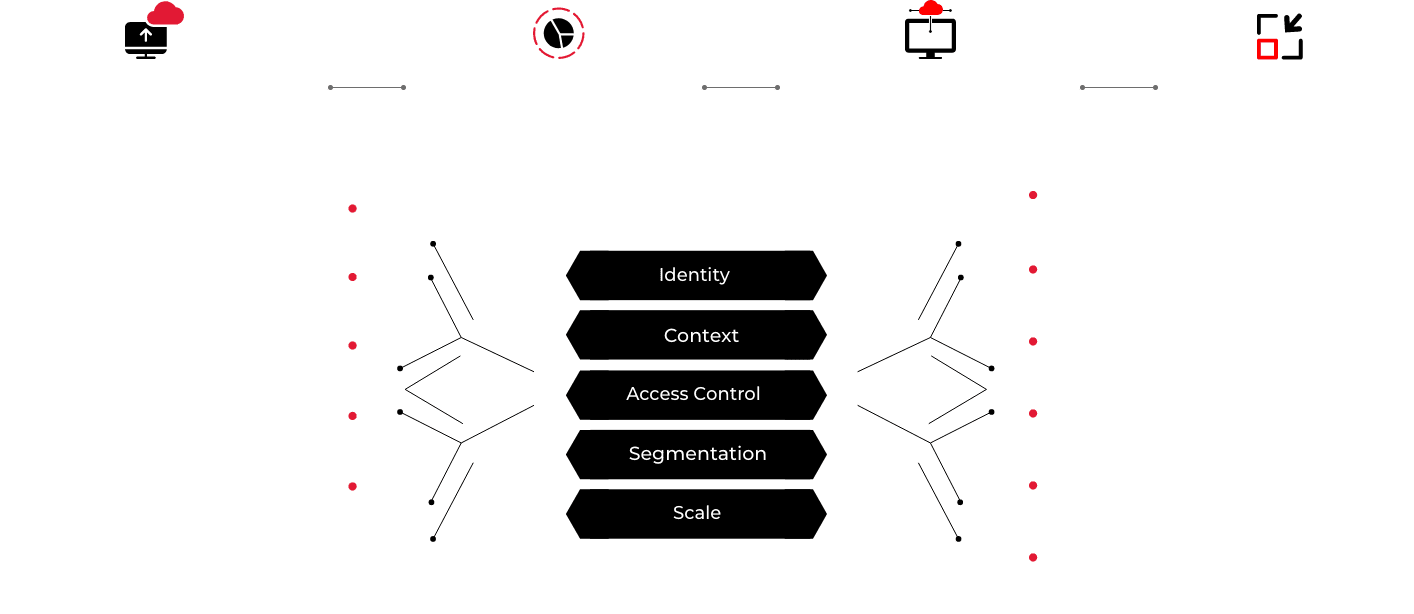
Secure direct access to applications as an alternative to VPN
Access based on Zero Trust principle: full user authentication and device security posture verification before connection
Dark cloud: no inbound connections, applications invisible to hackers and unauthorized users
Augments or replaces VPN to achieve higher security and cloud scale access


No infrastructure or architecture constraints
No VPN required for access, no network or firewall configuration changes
Simple user onboarding and experience, both on and off the network
Seamless integration with multiple identity providers (Okta, Ping, Azure AD) for authentication and single sign-on
Zero Trust access to cloud infrastructure services and workload micro-segments for example, Kubernetes, AWS, Azure, S3 buckets etc.
Secure access to critical applications and application segments in data centers
Specialized access for IT admins and DevOps /developers to affect separation of duties


Fully distributed SaaS cloud brokers deployed across the globe on public clouds
Connecters front-end protected resources and can be deployed on-prem or in the public cloud; available for AWS, GCP and Azure
Connectors are autoconfigured for easy onboarding
After successful user authentication and device health checks, the broker remains in the path while it seamlessly connects the user to the application

Centralized authentication, policy management and enforcement based on user identity, role, location, device health, and application context (risk score)
Least-privilege policies enforced regardless of user being on-prem or off-prem
Full network visibility into users, devices, applications with ability to drill down

Deep integration with Xshield identity-based segmentation for maximum security of applications and services being accessed by corporate and third-party users
Common policy model with full layer 7 context and awareness from device to user to application/workload/micro-segment
ML-based policy recommendation model makes it easy to define and manage policies

Verifies security state for every connection before connecting to application or resource
Dynamic real-time updates to access policies based on context and events
Custom quarantine templates for resource access based on device health, and criticality

Learn More
By submitting this form, you agree to ColorTokens
Terms of Service and
Privacy Policy