 Become a Partner
Already a partner ? Login
Become a Partner
Already a partner ? Login
Program
Partner Program Overview
Designed to deliver unparalleled customer value and accelerated mutual growth by harnessing partner expertise and ColorTokens cybersecurity technology.
Learn MoreInfrastructure
Quick Links
Case Study
Industry Solutions
Quick Links
Program
Designed to deliver unparalleled customer value and accelerated mutual growth by harnessing partner expertise and ColorTokens cybersecurity technology.
Learn MoreFeatured Topic
Newsletter
Over 75% of all network traffic today is lateral or East-West. Most traditional security solutions barely provide visibility into this traffic. This gaping blind spot allows attackers who have penetrated the perimeter defenses to remain undetected for months, while they move laterally targeting endpoints, applications, and workloads.
To overcome this challenge, the ColorTokens Security Platform (CTSP) provides unprecedented visibility into cross-segment traffic that was hitherto invisible to most security solutions. With CTSP, security teams are able to visualize all communications within their network, including users, endpoints, applications, and workloads operating in a hybrid data center environment.
The ColorTokens Xtended Zero Trust Platform shows network traffic between any two endpoints as a line between those nodes. The color of the line is used to indicate the trust level of the traffic is as per defined policies. A red line, for example, would be used to indicate that the traffic was “unauthorized”, i.e. against the policy mandates. And a green line would represent “conformant” traffic. In case, during a given time period, the traffic between two endpoints consists of a mix of both, an orange line is shown.
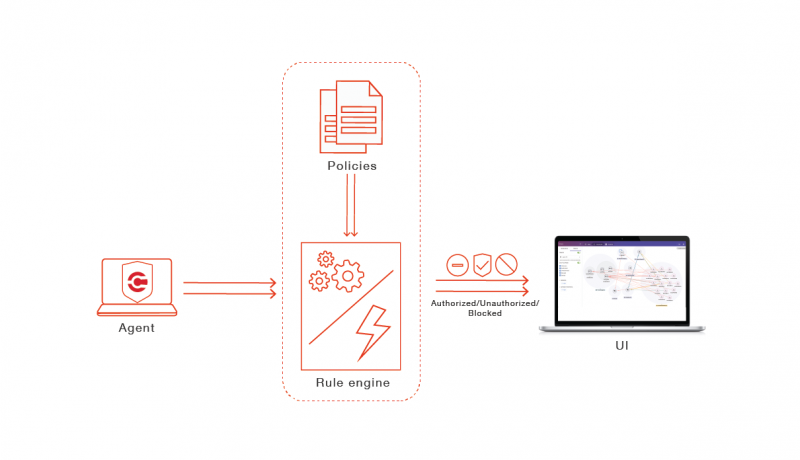
The platform implements zero-trust visualization by categorizing traffic as “allowed”, “denied”, “unauthorized” and “blocked”. The process begins by installing the CTSP agent on servers and endpoints. The agent generates records for all traffic to and from the endpoints. On the other end, a controller called the CTSP ColorMaster implements an independent verification module to determine if the traffic reported is conformant to the policy or not. The implementation consists of a highly optimized rule engine which runs the policy rules on each traffic record and determines the “trust” result for the traffic.
For example, if an endpoint reports the traffic sent on the network as “allowed”, the rule engine in the ColorMaster checks the policy applicable on that endpoint independently and determines if that traffic “should have been allowed” or not. If the traffic should be allowed, then the “trust” result for that traffic becomes “allowed”. Else it is marked as “unauthorized”.
However, you might ask how an endpoint can allow traffic which should not have been allowed. This happens under the following two scenarios:
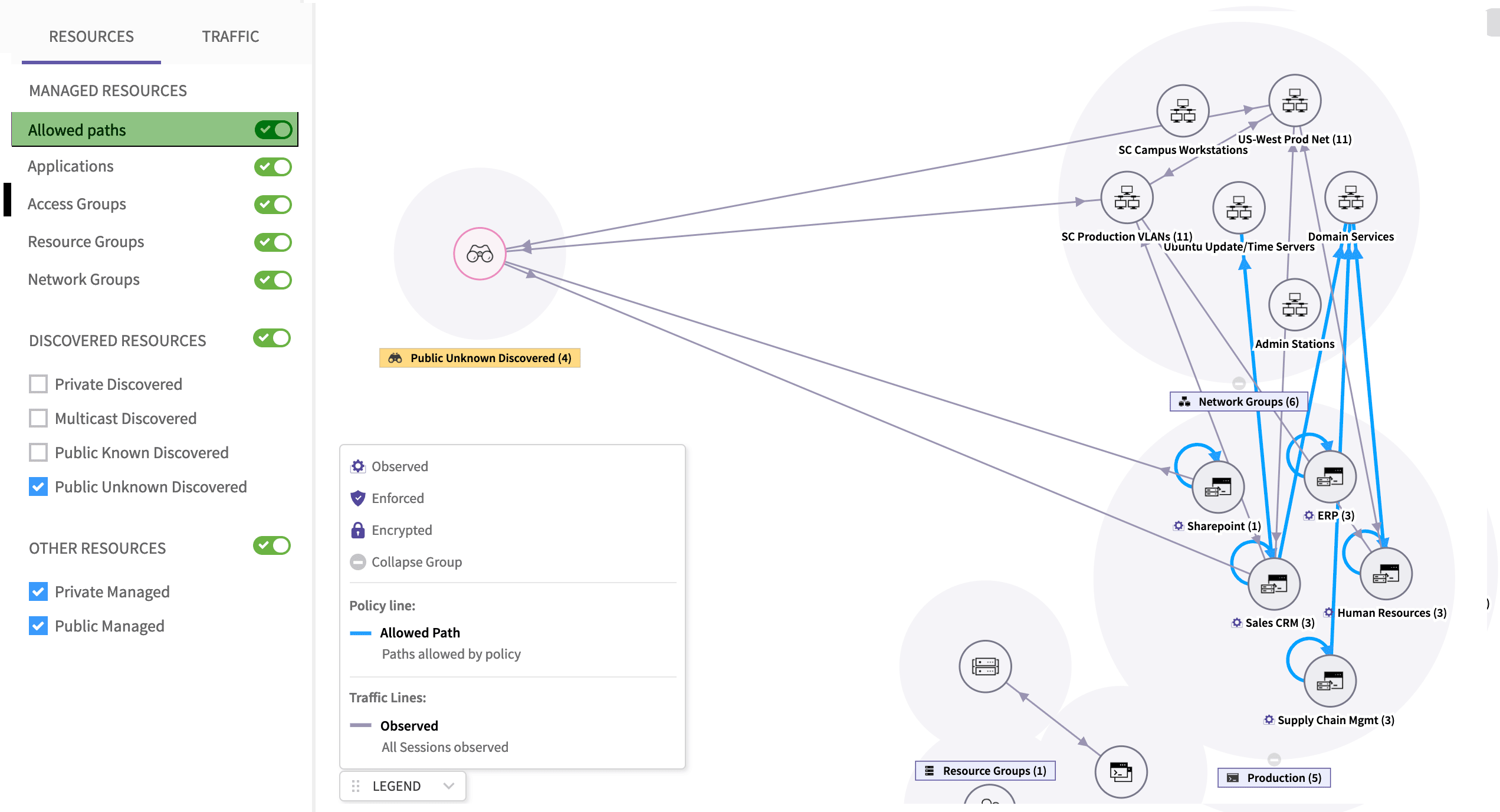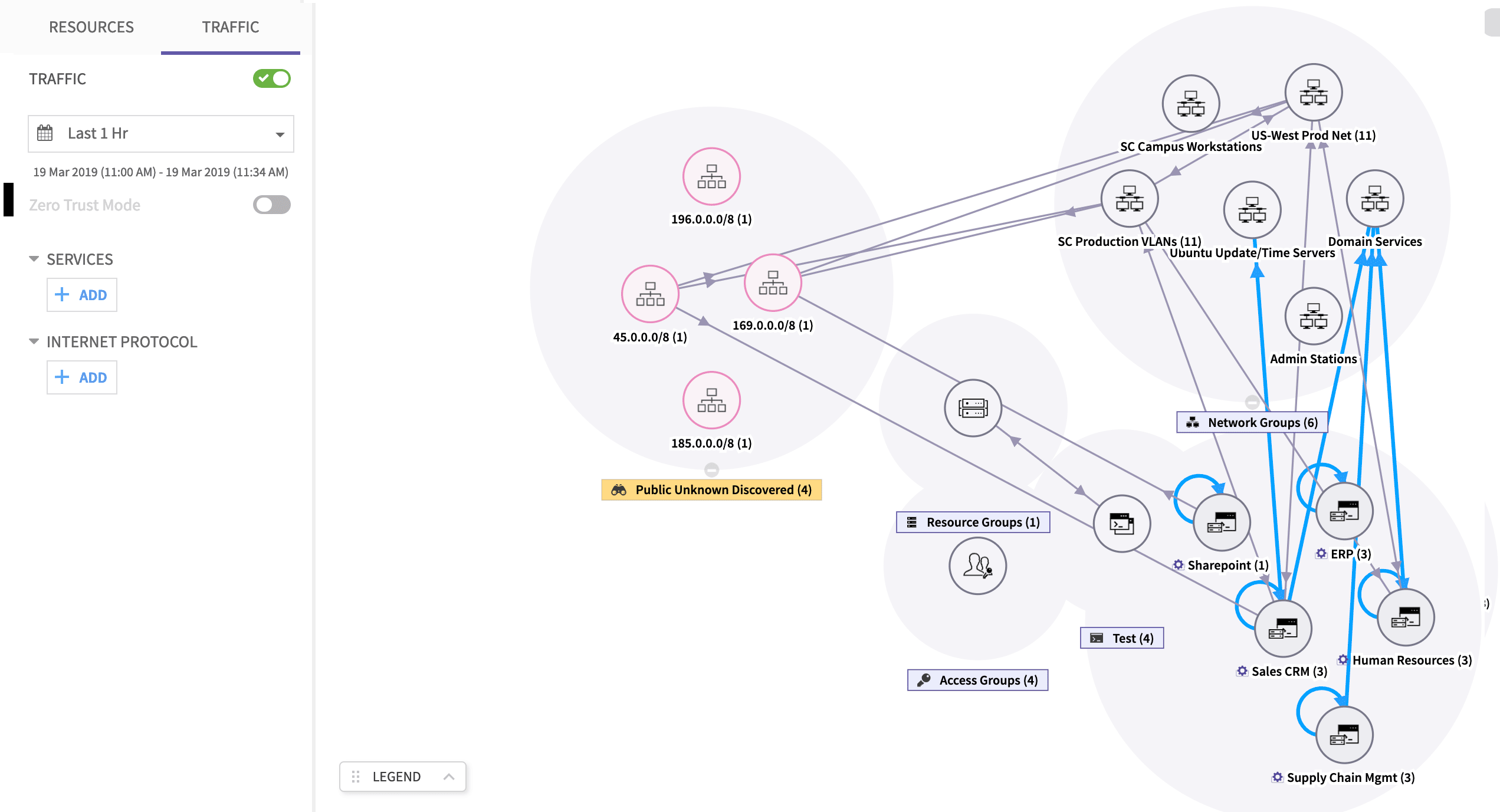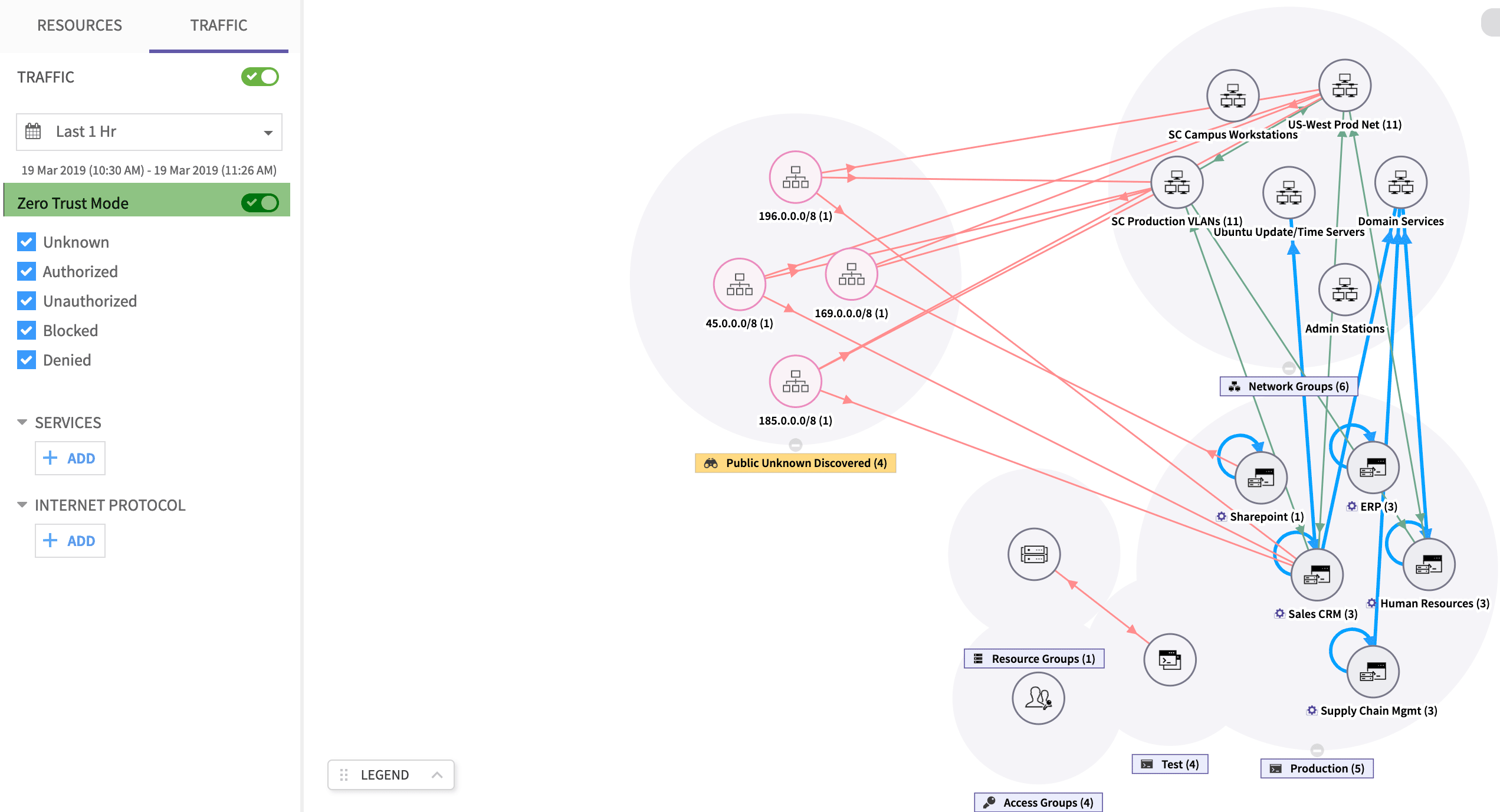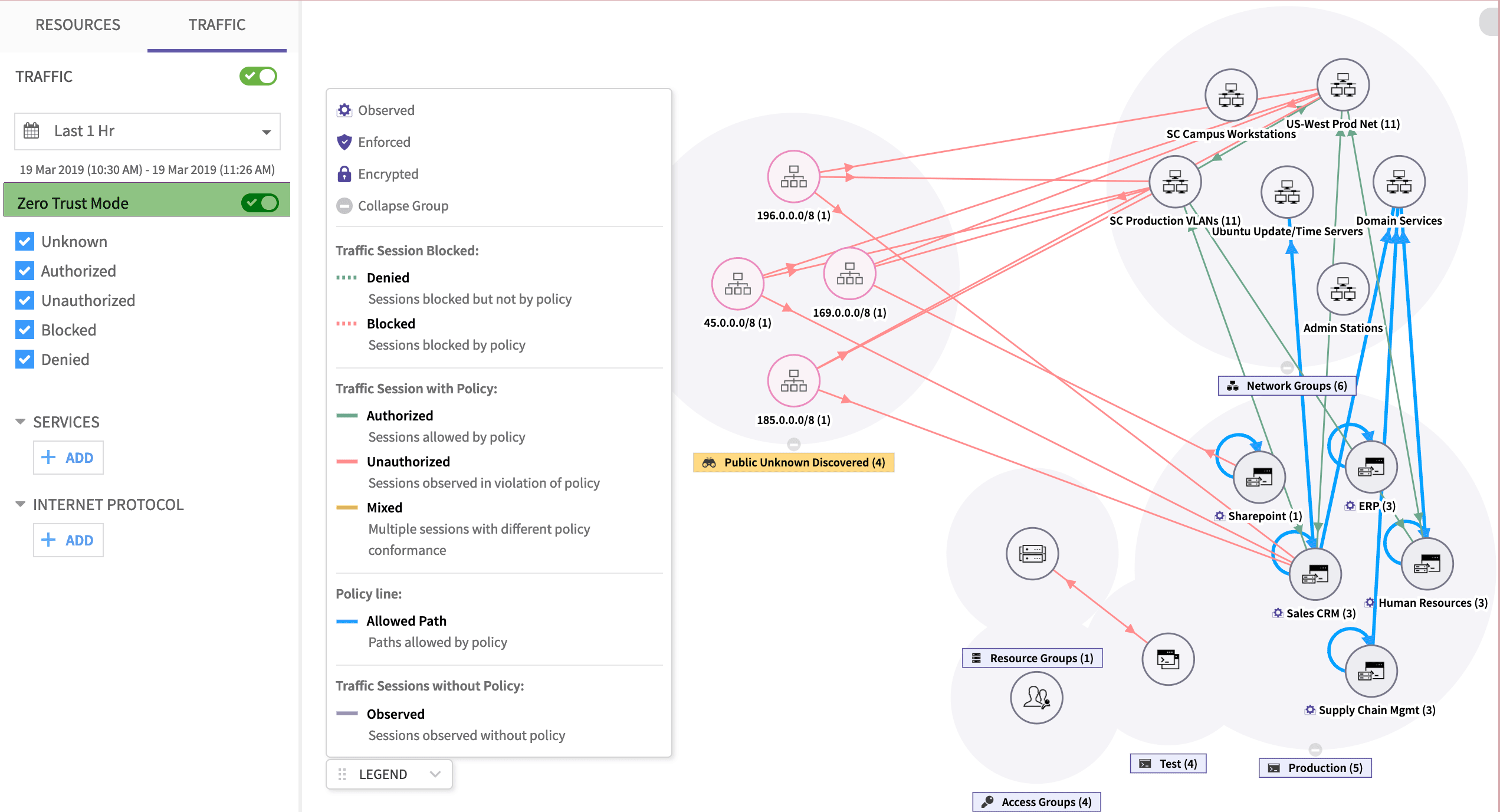
During the initial deployment, it is very likely that the enterprise will use visualization to understand what traffic is going on in their network. The security teams would start without policies and the system is configured in an “observation” mode. The CTSP agent at the endpoints would report traffic as “allowed”. But the rule engine, which cross-checks the policies, will mark them “unauthorized”. This would result in all traffic being marked with red lines. Since a zero-trust based microsegmentation uses a traffic whitelisting methodology, the absence of any rule to allow traffic implies traffic must not be allowed.
Now, based on expected traffic, the enterprises’ administrator can start defining policies. When the administrator starts to do this, some lines would turn green, some may turn orange. And some may continue to remain red. The administrator can now inspect the traffic details to determine what flows are escaping the currently defined policies. Usually, this is the stage where the administrator starts to get information on “unexpected” traffic flowing in the network. Thus, zero-trust visualization makes it easier for administrators to understand unexpected traffic (hence, unexpected applications) present in their network.
As the administrator investigates further, more whitelist rules may be added to allow some more traffic to flow. As for the rest, the administrator can initiate corrective actions. Therefore, even before proceeding to enforcement, the enterprise administrator gets both visibility and control over how their network is being used. They can now proceed to enforce to prevent compliance violations.
Due to bugs in applications, it is possible that endpoints may get compromised, providing a remote backdoor. Such backdoors are used by attackers to scan for other vulnerable endpoints and for lateral movement. However, traffic needs to be allowed for a scan to occur. The attacker may achieve this by tampering with the firewall rules at the endpoint. While the CTSP agent detects and rectifies the firewall quickly, it is possible some traffic has been exchanged. The rule engine in ColorMaster will accurately flag this traffic as “unauthorized” and generate an alert to indicate tampering.
In summary, zero-trust visualization provides enterprises with an effective tool to both understand and take control of their network and implement effective microsegmentation policies.
Learn more about ColorTokens’ network visualization and security here.
By submitting this form, you agree to ColorTokens
Terms of Service and
Privacy Policy