 Become a Partner
Already a partner ? Login
Become a Partner
Already a partner ? Login
Program
Partner Program Overview
Designed to deliver unparalleled customer value and accelerated mutual growth by harnessing partner expertise and ColorTokens cybersecurity technology.
Learn MoreInfrastructure
Quick Links
Case Study
Industry Solutions
Quick Links
Program
Designed to deliver unparalleled customer value and accelerated mutual growth by harnessing partner expertise and ColorTokens cybersecurity technology.
Learn MoreFeatured Topic
Newsletter
No, I’m not talking about the jet engine-like roar of server fans or the constant humming sound emanating from cooling ducts. I’m referring to the continual network chatter between endpoints, servers, and virtual machines in your enterprise networks. Most of us are unaware of this, but I see evidence in most enterprise networks where I deploy ColorTokens Xshield microsegmentation agents. A network engineer at one of my customers looked at the maze of traffic lines and coined the phrase “network noise pollution,” which stuck with me.
Much of this chatter is unnecessary traffic; some are older protocols that have since been replaced by more efficient and secure alternatives, and others that crossed over from the convergence of consumer and enterprise operating systems.
Here’s an example of a portion of an enterprise data center where I deployed the ColorTokens Xshield sensors. The lines indicate traffic flows within the last seven days, and we were awed by the volume of connections between the servers.
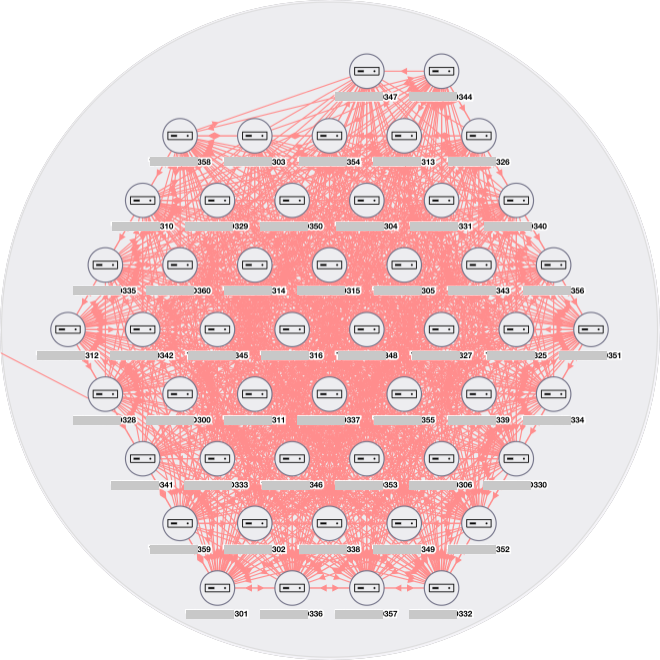
Traffic visualization showing all traffic, including network chatter
A quick analysis revealed the vast majority of connections to be Link-Local Multicast Name Resolution (LLMNR), Universal Plug and Play (UPnP), and Web Services Dynamic Discovery (WS-Discovery). None of these protocols were necessary in the environment and were present simply because they were not disabled in the base configuration of the systems.
We used Xshield’s visualization filtering capabilities to remove this “noise” and got a better picture of the environment.
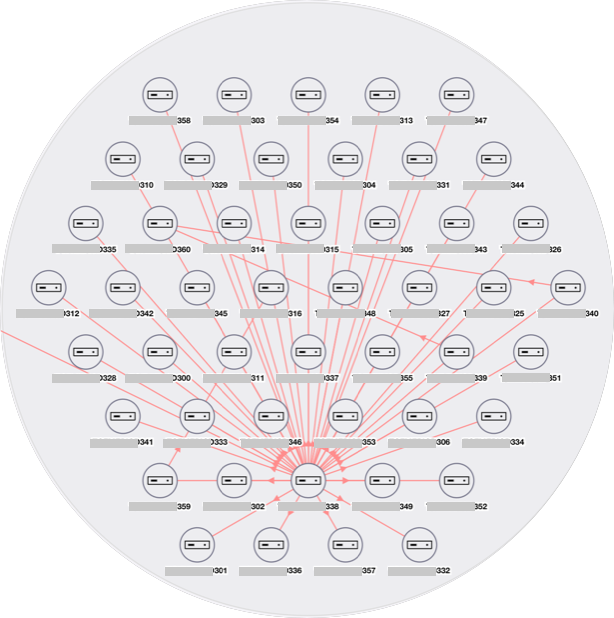
Traffic visualization after hiding LLMNR, UPnP and WS-Discovery
Unnecessary traffic and “noise pollution” aside, some of these protocols need to be disabled due to their security risks. Eliminating unnecessary traffic will also reduce the number of events sent to your SOC, reducing alert fatigue and your SIEM bill!
The respected folks at Black Hills Information Security have often discussed the risks of these protocols, including one titled How To Disable LLMNR & Why You Want To. The follow-up comments are equally interesting and discuss why these protocols are sometimes necessary to support legacy applications.
Turning off these protocols in large enterprise networks may be challenging. Using Active Directory Group Policy is an option, but what if only some systems should be targeted? And how do you verify if the fix is working?
The ColorTokens Xshield Microsegmentation platform provides a simple and scalable method to visualize such traffic and suppress these protocols at the source or destination without re-configuring the operating system or software on individual systems. The host-based Xshield agent uses the Windows Filtering Platform to selectively block the transmission or reception of these protocols without explicitly turning off the underlying service. Furthermore, the Xshield Management Console makes it easy to push these policies to any set of systems and test their operation before enforcement.
If you are concerned about the security risks of older protocols in your network environment and want to use Microsegmentation techniques to mitigate such risks, contact us.
By submitting this form, you agree to ColorTokens
Terms of Service and
Privacy Policy