 Become a Partner
Already a partner ? Login
Become a Partner
Already a partner ? Login
Program
Partner Program Overview
Designed to deliver unparalleled customer value and accelerated mutual growth by harnessing partner expertise and ColorTokens cybersecurity technology.
Learn MoreInfrastructure
Quick Links
Case Study
Industry Solutions
Quick Links
Program
Designed to deliver unparalleled customer value and accelerated mutual growth by harnessing partner expertise and ColorTokens cybersecurity technology.
Learn MoreFeatured Topic
Newsletter
A version of this article was originally published on CyberDefenseMagazine.com
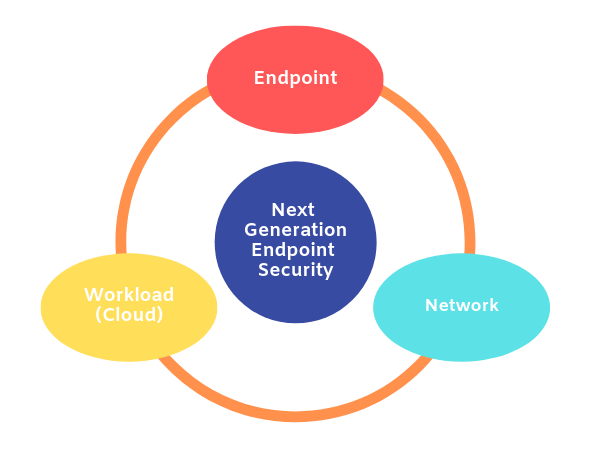
Traditional endpoint security control has always been about malware, threat analysis, and remediation. However, even the most pristine and clear endpoint will continue to become polluted after cleanup if the overall protection solution fails to take into consideration the context of its environment. An endpoint protection solution with a narrow focus on files, sequences, and malware residing on the endpoint—one that does not understand the network it belongs to, the user who sits behind the endpoint, or the application that user is trying to access—is, simply put, missing the point.
The endpoint security market is now on the cusp of significant innovation and change. A next-generation endpoint security solution must be able to recognize the user behind the endpoint and know how he or she should behave. It also needs to have a deep understanding of applications to verify the correct roles and access for each user.
Network security vendors have traditionally performed some of these functions, but unfortunately, this is not an ideal arrangement for today’s environment. The disappearing network perimeter and workload migration to the cloud have made perimeter security controls, like on-premise firewalls, limited in usefulness because they are not always in the path of communication. Similarly, the rising use of encryption will continue to make these networks increasingly dark, since they cannot effectively decrypt traffic at high speeds.
Security vendors have tried to bridge gaps between the network, endpoint, user, and application by bringing in a multitude of boxes in the network layer and a multitude of agents at the endpoint level in hopes that they will talk to each other and solve the problem—but this approach has yet to achieve the desired result.
Historically, endpoint security involved comparing an endpoint with a signature in a database. The signature database was initially downloaded from a central server to a local server in the organization. Every endpoint would then crosscheck file-hashes on its system against signatures in the database to determine whether a file was malicious or not. As the signatures expanded to include billions of hashes, databases grew larger and started moved to the cloud, where a central database served as a repository of all known good and bad file hashes.
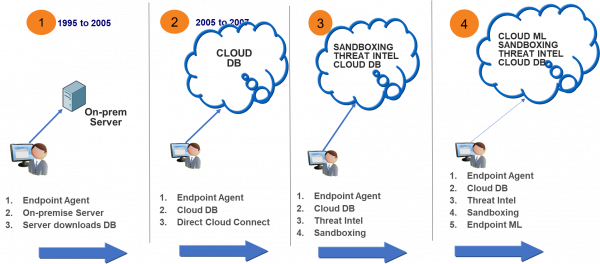
However, this database migration failed to solve the problem of zero-day malware, which by definition is a malicious file that has not been seen before and therefore does not have a hash in the cloud. To solve this problem, organizations deployed machine learning and sandboxing solutions. Sandboxing solutions simply played or executed this unrecognized zero-day file in a safe environment where its behavior could be analyzed for malicious characteristics. Likewise, machine learning was used to examine files that had taken source code from a known exploit but changed the code a bit to create a new executable, and hence a new hash. This form of attack, where the perpetrator changed a known malware slightly to create a brand new malware with a new hash value but essentially the same source code, was called “polymorphism.”
The security industry changed with Operation Aurora, a series of cyber-attacks conducted by a nation-state against well-known technology companies by a nation-state. Operation Aurora exploited a familiar vulnerability within Internet Explorer to spawn a PowerShell that could be used to execute commands on the target system. The earlier approach of crosschecking file hashes could not protect against these attacks, because Internet Explorer and PowerShell were legitimate commands; it was the sequence that was illegitimate. Under normal circumstances, a browser could spawn another browser, or a music player, but it should not be spawning a PowerShell.

The rise of nation-state attackers who repeatedly infiltrated each other’s private enterprise systems, as well as critical sectors such as finance and energy, contributed to the evolution of endpoint detection and response (EDR) solutions.
EDR tools work by monitoring endpoint and network events, and recording the information in a central database where further analysis, detection, investigation, reporting, and alerting take place. These solutions include four components:
It all starts with recording everything at the endpoint – every file access, every registry call, and every network connection is recorded from the endpoint and sent to the cloud. These actions are stitched together and scanned for malicious or suspicious sequences of activities, such as an internet browser spawning a PowerShell. In addition, an attacker running port scans and scanning systems laterally using known Windows utilities, who would normally evade signature defenses, would be caught by an endpoint detection and response system because his behavior would trigger an alarm.
For effective detection, most EDR solutions provide threat-hunting tools to scan data coming from millions of endpoints in order to see the spread of the infection or malicious intruder activity. They allow the administrator to then remediate the infected endpoint by providing tools such as a remote shell where the administrator can login to the infected endpoint and remove the malicious files.
However, EDR solutions also have certain limitations. Customers and solutions can become overwhelmed with the amount of data that must be recorded and analyzed to see malicious behavior, making remediation increasingly challenging. The volume of data grows as a company increases its headcount: more employees generate more data. This is why EDR solutions often package managed security services along with their product. Most customers are not equipped to handle the complexity of managing a Security Operations Center and personnel who can analyze large amounts of data.
An ounce of prevention is worth a pound of cure: if a doctor suspects you might have a severe food allergy, he or she doesn’t encourage you to eat whatever you want and then come back for treatment when you have a bad reaction. Rather, your doctor recommends you avoid the foods that could make you sick. The same concept applies to security. Rather than allow the user to run every possible application and every possible sequence of commands and then consult the cloud to determine whether a sequence was malicious or not, an alternate approach would be to simply block users from initiating certain sequences of actions or running certain applications.
Whitelisting and blacklisting techniques are extremely effective in fixed function devices and environments with a limited change to the endpoints. Under these circumstances, it is much easier to simply analyze all the running processes, create a set of process controls, and lock the device down. With this approach, rather than scanning for all possible bad sequences, vendors prefer to limit systems to known good behavior. Any new process created outside the known “white list” of allowed processes triggers an alert or is blocked before execution. Likewise, any process which triggers a network connection other than the well-known utilities like a browser or a file transfer utility will trigger an alert or be stopped prior to execution.
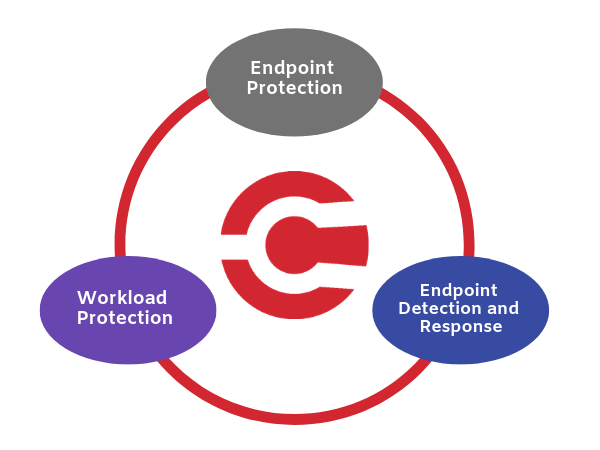
At ColorTokens, we want to bring the power back to the endpoint—and make it smarter. The endpoint is the start of any communication and, therefore, the best place to enforce security. We start by sitting at the endpoint in order to understand the user who is at the endpoint, their access permissions, what applications they use, and of course all the files they download as payload using these applications. The rest of the endpoint security is about analyzing the files they download into the endpoint and examining the malicious behavior of the payload.
ColorTokens Xprotect analyzes files using traditional Endpoint Protection Controls. We record events to ensure that some malicious sequence is not skipped. However, we also add sophisticated whitelisting, blacklisting, and process controls. If a user is accessing a risky file-sharing application that downloads malware to the system, we do not wait for it to happen and then try to recover like a traditional endpoint security solution. We apply user and application context to the endpoint, enabling it to quickly recognize and halt risky behavior. We can always revert to the traditional endpoint security behavior of seeing the malware and cleaning it up or preventing its execution, but we first and foremost try to prevent the bad behavior from happening to begin with.
The ColorTokens platform can be deployed across any endpoint or workload in the cloud (Amazon, Azure, and other vendors) and addresses the complete network and endpoint context in one simple, easy-to-use solution.
By submitting this form, you agree to ColorTokens
Terms of Service and
Privacy Policy