 Become a Partner
Already a partner ? Login
Become a Partner
Already a partner ? Login
Program
Partner Program Overview
Designed to deliver unparalleled customer value and accelerated mutual growth by harnessing partner expertise and ColorTokens cybersecurity technology.
Learn MoreInfrastructure
Quick Links
Case Study
Industry Solutions
Quick Links
Program
Designed to deliver unparalleled customer value and accelerated mutual growth by harnessing partner expertise and ColorTokens cybersecurity technology.
Learn MoreFeatured Topic
Newsletter
Most of today’s organization’s data center deployment and operations are incredibly complex, as they not only have their own business-critical applications but also host their customers’ data. This presents a critical challenge in securing both their own and their customers IP.
To add to this complexity, these data centers will be a combination of on-premises, shared, or outsourced to a third-party data center for management and operations. Many customers host horizontal applications that are tenants of a larger data center that need to be separated from other workloads and customer environments.
For example, PCI-compliant credit card or POS machines in a retail corporation are horizontal applications that are unique tenants sharing the same infrastructure. Although in this multi-tenant environment, these machines reside in the same infrastructure, it is critical that each pod/machine/environment is isolated from corporate business applications and other customer environments.
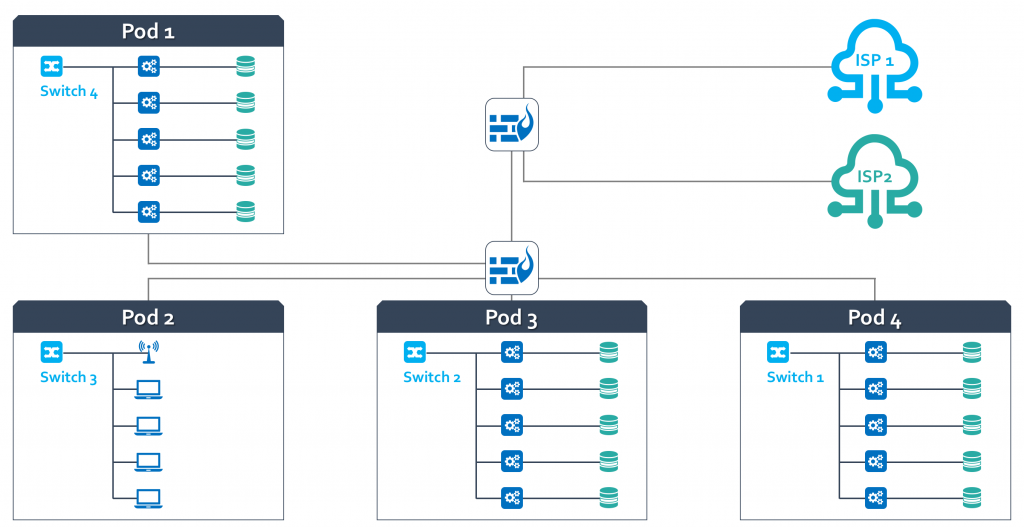
Today, most customers will separate environments by creating a physical or virtual pod environment for their own and their customers’ needs. The environments are then typically segmented using VLANs, but as the environments and workloads scale you will run into one of the following scenarios:
In both scenarios, you face an incredible operational expense, and the ongoing management of the configuration will be painful.
To achieve microsegmentation in multi-tenant scenarios, your solution should be easy to implement and operate and provide you with the following:
See how ColorTokens’ award-winning security solutions can help improve your organization’s security posture. Register for a free demo today!
By submitting this form, you agree to ColorTokens
Terms of Service and
Privacy Policy