 Become a Partner
Already a partner ? Login
Become a Partner
Already a partner ? Login
Program
Partner Program Overview
Designed to deliver unparalleled customer value and accelerated mutual growth by harnessing partner expertise and ColorTokens cybersecurity technology.
Learn MoreInfrastructure
Quick Links
Case Study
Industry Solutions
Quick Links
Program
Designed to deliver unparalleled customer value and accelerated mutual growth by harnessing partner expertise and ColorTokens cybersecurity technology.
Learn MoreFeatured Topic
Newsletter
In our day-to-day interactions here at ColorTokens we spend a lot of time talking to our principal customers who are typically the CISO, or IT Infrastructure lead. They’re our natural customer-advocates because of our role as the manufacturer of cutting-edge zero trust cybersecurity software. We know how to support the CISO and speak with him or her in a language that we all understand. But we also know that that the ultimate stakeholder for our zero-trust security solution isn’t our obvious customer, the CISO. It’s really the CISO’s stakeholders: the application owners, C-suite peers, and the board of directors. In a phrase, we know that our customer has a customer of their own, and knowing this is crucial.
Today, many CISOs report to the CIO, CFO, or CEO. The CISO doesn’t often get direct feedback from their stakeholders on the Board of Directors. In fact, he or she may have only one shot in a quarter—or even in a half-year—to articulate to the BoD how the team is addressing their cybersecurity and resilience goals, and how that furthers the company’s overall strategic plan. These stakeholders aren’t interested in technical reports detailing the number of endpoint agents installed, number of servers segmented, or number of traffic policies enforced. Instead, the C-suite and Board of Directors are interested in quantifiable improvements in their company’s resilience and sustainability. The CISO must justify the company’s investments in cyber security. They’re interested in audit readiness, and they want to see a quantifiable reduction in risk. They want to know how the company is prepared for the upcoming SOC audit, ISO 27001 compliance, or ESG audit (the cybersecurity score can be the difference between ESG silver and gold status).
How does ColorTokens help with this? One way is by providing the enabling technology to create a cyber security posture that is adaptive to evolving compliance audit requirements and resilient to ever-changing threats.
First, we enable the CISO to show how the cyber security program has instituted the fundamental concepts of zero trust security: assume a breach, gain visibility across the entire network, provide secure user access to network resources, and stop lateral traffic of malware and ransomware. We provide clear metrics that are understandable by the stakeholders – the percentage of decrease in attack surface and ability to move across the network, as well as blocked threats benchmarked against industry standards. This shows how the CISO’s initiatives support the resilience and sustainability that is so important strategically for the company, not to mention audit and regulatory bodies. Fundamental zero-trust security makes the company ready for any change that regulators impose, and whatever new threats attackers present.
Then, we provide log files for audits and graphical reports like the one below that lets the CISO demonstrate continuous incremental improvement in the actual cyber security posture. These reports, which address the true goals and concerns of the ultimate customer, can help our CISOs and IT Infrastructure Managers address the strategic needs of the organization.
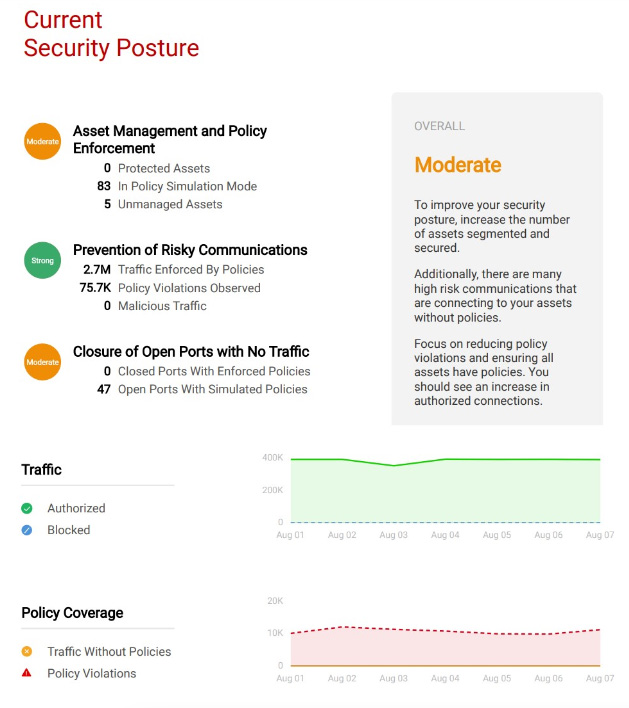
And finally, if your company is just beginning the journey to a zero-trust architecture, we have a useful offering: the Cybersecurity Posture Assessment. This is a consultancy engagement that gives you a solid starting point for a successful zero-trust cybersecurity initiative. It helps you build the business case for your stakeholders for your cybersecurity implementation project. The delivered assessment provides you with an understanding of the current state of your security posture, the desired state, and the gap. It empowers you with concrete implementation steps you can use to help move your organization forward towards a zero-trust security maturity model, with the benefits of increasing the security of your critical applications and precious enterprise data. It lets you comply with audit and regulatory standards.
Your organization’s cyber security posture will be measured along six dimensions for the assessment:
The cybersecurity posture is scored using more than 200 control criteria which are primarily derived from Center for Internet Security’s (CIS) top 20 controls, the National Institute for Standards and Technology (NIST) Cyber Security Framework, and the Capability Maturity Model Integration (CMMI) standard framework, as well as ColorTokens’ point of view on the desired capability level for every sub-control based on our experience working with multiple client organizations in several diverse geographies and industries.
Conclusion:
At ColorTokens, we recognize the importance of engaging stakeholders beyond the CISO, empowering organizations to address resilience, sustainability, and compliance goals. By embracing fundamental zero-trust security principles, providing clear metrics, and offering a Cybersecurity Posture Assessment, we support organizations in their journey toward a secure and protected enterprise.
We’re ready to support you in your mission to address your stakeholder’s strategic needs of resilience, sustainability, and compliance. Give us a call to learn more or go to www.colortokens.com.
By submitting this form, you agree to ColorTokens
Terms of Service and
Privacy Policy