 Become a Partner
Already a partner ? Login
Become a Partner
Already a partner ? Login
Program
Partner Program Overview
Designed to deliver unparalleled customer value and accelerated mutual growth by harnessing partner expertise and ColorTokens cybersecurity technology.
Learn MoreInfrastructure
Quick Links
Case Study
Industry Solutions
Quick Links
Program
Designed to deliver unparalleled customer value and accelerated mutual growth by harnessing partner expertise and ColorTokens cybersecurity technology.
Learn MoreFeatured Topic
Newsletter
Detecting threats that already exist in the network environment is difficult in comparison to the newer threats. Advanced Persistent Threat (APT) is an umbrella term for attacks where an intruder or a group of intruders have already established a long-term presence in the target network – without being detected, hidden in plain sight!
According to Ponemon Institute’s 2017 Cost of Data Breach Study, it takes organisations 191 days to detect a data breach. In most cases, these kinds of attacks are triggered to steal data or spy on the target network. APT attacks are systematic; unlike traditional cyber-attack, they require planning, manpower, and computing resources. If successful, the damage they create is huge.
Some of the attacks which have used this mechanism are Titan Rain (2003), Ghostnet (2009) and Deep Panda (2015). More recently, in August 2018, a bank in India was targeted by hackers who simultaneously withdrew $13.5 million through ATMs across 28 countries over a single weekend.
Such attacks were primarily established to spy on the target network and steal sensitive data or money from the target organization. APTs can be also used for stealing intellectual property, sabotaging the internal structure of an organization or sometimes even taking over a complete site.
The host network discovers these attacks only when the damage has been already done. APT attacks are not random. Rather, these attacks are pre-planned, and targets are chosen after extensive research. APT attacks are highly complex in nature compared to web application attacks.
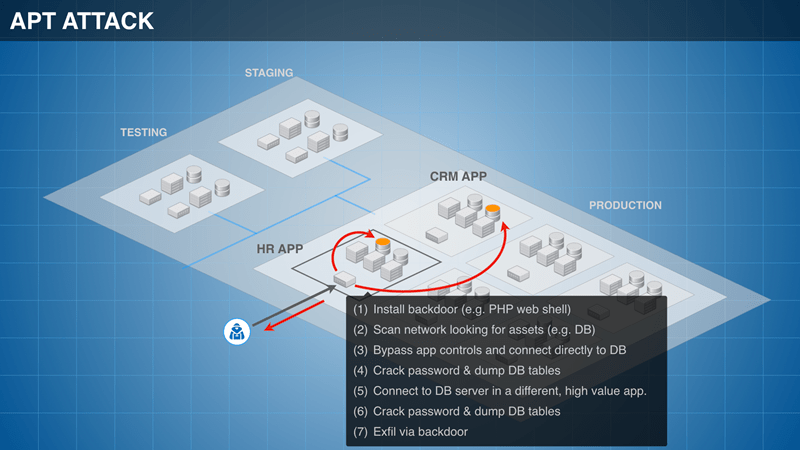
An APT attack is characterized by a ‘Cyber Kill Chain’, where the attack is divided into four different stages.
The target information is gathered. This includes critical information such as open ports, network ranges, active machines, network mapping etc.
The initial infiltration is done with the help of a common form of attacks such as SQL injection, remote file inclusion (RFI) and cross-site scripting (XSS).
Trojans along with the backdoor shells are used to gain a foothold on the target and gain persistence in the target network. At this stage, malware might be used to exploit various forms of vulnerabilities in the network. A modern-day attacker makes use of fileless malware to attack the target network. In the case of fileless malware attacks, no physical file or software used. Instead, the capabilities of the target operating system are hijacked by attackers and tuned to attack its own network. For the conventional firewall or antivirus program, it is extremely difficult to detect the fileless malware due to the absence of a required signature. This is why fileless malware is often used for ransomware attacks, as it is difficult to detect. Once the persistence is established in the network, the network is controlled externally by the attacker.
In the fourth stage, the attacker might silently spy on the network, and look for the necessary data which needs to be extracted. Once the data has been transferred to an external server, the attacker will exfiltrate from the network.
It’s is tough to contain APTs with traditional security solutions like perimeter firewalls, internal firewalls, and VLAN/ACLs because they provide limited visibility into the network. One of the most effective ways to combat APTs is by implementing a unified security solution that provides a combination of granular visibility and microsegmentation.
Visibility of the complete network provides a map of all communications between endpoints, servers, and business-critical applications. If an endpoint, for example, is trying to talk to a server it is not authorized to, it can be flagged immediately for suspicious activity. This leads to the detection of both existing and any new threats trying to infiltrate the network.
Another characteristic of APTs is that they move laterally by exploiting open ports and gaps in firewall rules. This lateral movement can be contained by microsegmenting the network and applying intent-based security policies. Software-based microsegmentation can be driven down to the workload level to ensure that the attack surface remains minimal. What this means is that individual hosts can be segmented, and security policies applied so that even if one endpoint or application is breached, there is no way for the threat to move anywhere else in the network.
APTs are responsible for some of the most high-profile security breaches discovered in recent times. Along with financial losses, they cause irreparable damage to an organization’s reputation. Fortunately, new developments in security technology have the capabilities to detect and prevent APTs. But to do that, CIOs and security operators need to explore proactive security models like microsegmentation based on the zero-trust architecture that effectively protect data across the enterprise.
ColorTokens zero-trust architecture and intent-based security proactively secure workloads, application environments, users, and endpoints against advanced persistent threats.
By submitting this form, you agree to ColorTokens
Terms of Service and
Privacy Policy