 Become a Partner
Already a partner ? Login
Become a Partner
Already a partner ? Login
Program
Partner Program Overview
Designed to deliver unparalleled customer value and accelerated mutual growth by harnessing partner expertise and ColorTokens cybersecurity technology.
Learn MoreInfrastructure
Quick Links
Case Study
Industry Solutions
Quick Links
Program
Designed to deliver unparalleled customer value and accelerated mutual growth by harnessing partner expertise and ColorTokens cybersecurity technology.
Learn MoreFeatured Topic
Newsletter
Enterprises migrating to the cloud have applications and workloads with services and infrastructure distributed across public clouds, VPCs, campuses and/or data centers. Remote and local IT administrators and contract personnel need secure access to critical applications and infrastructure services with separation of duties per application, workload segment or service.
Applications and workload segments can span multi-cloud or hybrid cloud infrastructure environment. Using traditional VPNs is cumbersome and expensive.
Xaccess enables IT admin, whether employees or contractors, with secure access to distributed applications and infrastructure across any cloud or data center with zero complexity deployment and operations.
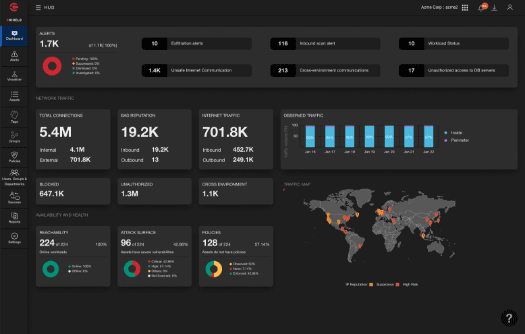
Take ColorTokens Xshield for a test drive.
See HowXaccess provides Zero-Trust based access to remote workload segments, services and infrastructure across any cloud, hybrid cloud or data center with zero complexity deployment and operations. Xaccess integrates seamlessly with Xshield to enable secure remote access with automated policy enforcement to dynamic workloads including Kubernetes, cloud infrastructure services, S3 buckets and other cloud services.

Xaccess makes it seamless and easy for IT to define and manage policies at scale across clouds. Access control and workload segmentation policies can be easily created with ML-based policy recommendations based on user, device, network, and workload context and viewed in a single console. IT can create user groups and policies tied to specific applications or micro-segments, whether those are data center applications, cloud native workloads or services.
Xaccess integration with workload-to-workload segmentation provides maximum, end-to-end security of applications and services being accessed by internal and external users. Granular and dynamic policies can be applied to both front-end and back-end access, and automatically updated to reflect change in context.
Learn More
By submitting this form, you agree to ColorTokens
Terms of Service and
Privacy Policy